The Astonishing Security State Travails of Our New Podcaster Barrett Brown
Barrett Brown was almost put away for over 100 years. His crime: publicizing documents that reveal the shadowy world of intelligence contracting in the post-9/11 era.
A Private Government
In a nation operating under the rule of law, one might presume that exposure of the “Team Themis” conspiracy would prompt official investigations of some sort, even if the proposed activities were in the planning stages. But the emails reveal a different role for the Department of Justice (DOJ).
At issue was the cache of documents from Bank of America that WikiLeaks was allegedly sitting on. BoA was understandably desperate to prevent their release, or at least mitigate the fallout from any revelations they contained. The big bank had a lot at stake: as of 2010, when these events were unfolding, Forbes ranked BoA as the world’s third-biggest corporation. It was also one of the Big Four publicly-insured “too big to fail” banking monoliths that dominate American finance (and politics).
As recipients of over $45 billion in the 2009 bank bailout via TARP (the Troubled Asset Relief Program) and given a federal insurance guarantee for nearly $120 billion, BoA was already facing a PR nightmare. It’s unclear what was in the cache of documents obtained by WikiLeaks, but it was enough to rattle BoA’s legal department, who approached the Justice Department on what to do next.
DOJ, under the supervision of Attorney General Eric Holder, recommended that BoA solicit the services of, you guessed it, Hunton & Williams.
The discussions between Team Themis and H&W involved some sordid and possibly illegal pursuits. One proposed method of undermining WikiLeaks was to “submit fake documents and then call out the error,” seemingly a plan to commit forgery and fraud—both felonies under the US code. Similar tactics to destroy WikiLeaks’s credibility were delineated in a 2008 Pentagon memo, which labeled the whistleblowing website an “enemy of the state.”
A ProjectPM researcher, Lauren Pespisa, told WhoWhatWhy in correspondence, “Team Themis was a collection of government intelligence contractors…hired by private clients to go after WikiLeaks, as well as labor unions who opposed the U.S. Chamber of Commerce—using offensive cyberwar techniques. They targeted many journalists and supporters of Wikileaks in order to discredit the organization, using methods most Americans would find reprehensible, and threatening to individual privacy.”
Indeed, in an email from Aaron Barr of HBGary Federal to Matthew Steckman of Palantir Technologies, Barr makes the case for subverting WikiLeaks and its supporters in the “liberal” media–and discusses plans to “attack” then-Salon columnist Glenn Greenwald.
Other tactics discussed in the emails include “cyber attacks against the [WikiLeaks] infrastructure to get data on document submitters,” noting that it “would kill the project.” Thus, the corporate representatives were advocating precisely the behavior the federal government has been on a crusade to prosecute, when others are doing it.
The conspiracy also called for “sustained pressure” through a “media campaign” to create “concern and doubt amongst moderates,” while discouraging whistleblowers by generating “concern over the security of the infrastructure,” and creating “exposure stories.”
Coordinating a propaganda campaign on behalf of clients is what firms like Hunton & Williams get paid for. But H&W explicitly solicited companies that have the technological means to violate the privacy of their targets, and quite possibly the law. The ability to “discredit” a journalist, as proposed, presumably hinges in part on blackmail material—just the type one can find in a substantive hack.
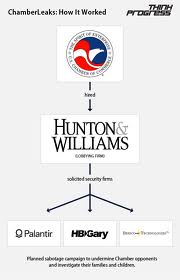 The Team Themis firms solicited by H&W all do sensitive military and intelligence contracting work for the government, and in many cases are creations of the government sectors for which they work. Berico Technologies, founded in 2006 by military veterans, lists among its products the Biometric Automated Toolset (BAT), the “Army’s flagship product for biometrics.”
The Team Themis firms solicited by H&W all do sensitive military and intelligence contracting work for the government, and in many cases are creations of the government sectors for which they work. Berico Technologies, founded in 2006 by military veterans, lists among its products the Biometric Automated Toolset (BAT), the “Army’s flagship product for biometrics.”
Another—Palantir Technologies—was founded in 2004 with funds from the venture capital firm, In-Q-Tel, to develop software for fraud detection. In-Q-Tel is a non-profit investment firm chartered in 1999 at the request of the CIA director. In-Q-Tel’s investment is run through In-Q-Tel Interface Center (QIC), an office within the CIA. Trustees from In-Q-Tel hold executive level positions at companies such as Netscape, Sun Microsystems, Time Warner, Federal Express, ATT Wireless, and New Enterprise Associates. Most of its current investments are in the biotechnology and IT/communications industries.
HBGary Federal was the offshoot of HBGary that did direct work for the government. While privately formed by Greg Hoglund in 2003, a computer security specialist, HBGary was then acquired by ManTech International in early 2012. As one of the leading software contractors for the Departments of State, Justice, Homeland Security, and Defense, as well as the nation’s 16 spy agencies, ManTech International has seen its yearly revenue rise by more than 600% between 2001-2010. ManTech is so embedded with the national security state that its employees are often placed inside the military units they support.
Flipping the COIN
The growth and ambition of the US military over the past decade has required a congruent growth in information operations against “enemy” populations. In this vein, the HBGary emails also discuss a project known as Romas/COIN. Renamed “Odyssey” in 2011, Romas/COIN was a contract originally held by defense giant Northrup Grumman.
The program was a military initiative to mine and store massive amounts of data from all across the Arab world: phone calls, social media interactions, Internet searches, among other data streams. The emails discuss collaboration by over a dozen firms—all with their own niche skills—to displace Northrup and win a “re-compete” for the contract. The emails even identify household names like Google and Apple as collaborators in the scheme.
Although the re-compete was eventually cancelled, and replaced with a new contract for the program known as “Odyssey,” there’s no reason to suspect the project has been discontinued. Two days prior to the HBGary hack, on February 3, 2011, key members of the firm consortium met with the contracting officer for Odyssey at a location known as “HQ.” The trail runs dry after the email hack, which clearly derailed their potential (or at least that of HBGary) to bid on the contract. As history shows us, the employment of technologies in theaters of war always precedes their domestic importation: from the telegraph and telephone in colonial Philippines to drones in Pakistan and Yemen. So it should come as no surprise that this type of data mining is hardly novel or confined to a particular government agency.
 National Security Agency (NSA) whistleblower William Binney has gone on record stating that NSA is actively creating dossiers on every single American citizen. Lt. Col. Anthony Shaffer, a former officer in the Defense Intelligence Agency (DIA, the Pentagon’s spy agency), has noted that when he served in the late-1990s his agency was actively utilizing such data-mining technology: “What we did then would take a year, you can do that in a minute [or] a matter of seconds now.”
National Security Agency (NSA) whistleblower William Binney has gone on record stating that NSA is actively creating dossiers on every single American citizen. Lt. Col. Anthony Shaffer, a former officer in the Defense Intelligence Agency (DIA, the Pentagon’s spy agency), has noted that when he served in the late-1990s his agency was actively utilizing such data-mining technology: “What we did then would take a year, you can do that in a minute [or] a matter of seconds now.”
Digital Puppeteers
In an age of online organization and activism, how do governments discourage private citizens from such uses of the Internet? Well, a tyrant can use the mailed fist and just shut off access to it. But the more refined autocrat would simply exploit the medium to create perception of public support for their position. Enter: Project “Metal Gear.”
Metal Gear is the term given by ProjectPM’s editors to “describe any methodology or apparatus…[used] with the intent of manipulating information or perception, conducting data mining, or infiltrating social organizations.” Crucially, it involves the ability to deploy fake online personas controlled en masse by a human operator—a phalanx of Facebook marionettes to sway public opinion.
This tactic of “sockpuppeting” is hardly new. PR firms are known to routinely employ fake personas to sell products or influence viewers in online forums. But the latest software developments here are astounding, allowing for a single operator to control up to fifty online personas (at least in the case of the United States Air Force’s [USAF] contract for the technology). As detailed in this 2007 patent, communications between the persona and its human targets can be regulated by software-based filters that assist in “maintaining situational integrity”—the puppeteer need not even move his fingers!
And these initiatives appear to be just the tip of the iceberg. Other evidence points to American PR firms using digital sabotage techniques against dissidents from Bahrain and Saudi Arabia, whose U.S.-friendly monarchies happened to be their clients.
Through ProjectPM, Brown was starting to map out the web of links and business arrangements among all these private cybersecurity contractors, not to mention the non-stop revolving door for key personnel between firms and the government for which they contract. But all that spadework ended when FBI agents stormed his residence on September 12, 2012.
The Mission, Not The Man
Perhaps the greatest irony in this case is the charge against Barrett Brown for “concealing evidence.” As his saga demonstrates, his real crime seems to have been revealing evidence.
Brown has been a point man in the ongoing effort to inform the American people about the consequences of the massive growth in the intelligence and military-industrial complexes since 9/11—and of the secret government at the heart of our weakened democracy.
Brown comprehended that the few avenues available to ordinary citizens for holding state actors accountable can be easily circumvented through a kind of deceptive privatization. He understood the importance of highlighting the inherently corrupt relationship between the state and the corporation. This included non-state entities handling dirty ‘official’ business on a deniable basis, and the state serving as an enforcement arm for big capital.
With much ado in recent days about Chinese cyber espionage, the government is using this new “Yellow Peril” as an opportunity to mount a full court press against the ability of any group to maneuver on the Internet in ways that might threaten corporate and state interests. The White House just announced a new administration-wide strategy to identify and prevent the theft of trade secrets, labeling WikiLeaks, LulzSec, and associated ‘hacktivist’ groups as dangerous in this regard.
“Disgruntled insiders [may leak] information about corporate trade secrets or critical U.S. technology to ‘hacktivist’ groups,” the document warns. The language is instructive; it makes no distinction between groups that may be receiving such leaked information to sell to the highest bidder and groups that want to release the information to the American people in order to blow the whistle on ‘insider’ waste, fraud, abuse, or illegality.
 Brown, and those close to him, also understand what the government was truly after when they stumbled into his life in March of 2012. The charges against Brown for harassing a government official, obstructing justice and concealing evidence may seem unrelated to his journalistic work, but the initial search warrant issued for his home on March 6, 2012, cast an ominously wide net. “The entities listed [there] are all things ProjectPM was looking into,” Gallagher confirms. “ProjectPM is [now] mostly defunct without [him].”
Brown, and those close to him, also understand what the government was truly after when they stumbled into his life in March of 2012. The charges against Brown for harassing a government official, obstructing justice and concealing evidence may seem unrelated to his journalistic work, but the initial search warrant issued for his home on March 6, 2012, cast an ominously wide net. “The entities listed [there] are all things ProjectPM was looking into,” Gallagher confirms. “ProjectPM is [now] mostly defunct without [him].”
Citing the extraordinary charges and the zeal with which the feds are operating, Brown’s supporters have set up a website to collect donations and fund a proper legal defense for him. With Brown in custody, much of his work has stalled. “[ProjectPM] was Barrett’s baby,” Lauren Pespisa laments. Although other websites such as Telecomix’ Blue Cabinet Wiki are attempting to pick up and expand on ProjectPM’s work, “that IRC has been suffering massive DDoS [attacks] and is very quiet. I fear ProjectPM may have been something special, I haven’t seen anything replace it yet.”
At our publication deadline, ProjectPM’s site was down for unknown reasons.
# #
Related front page panorama photo credit: Adapted by WhoWhatWhy from Barrett Brown (Free Barrett Brown / Wikimedia – CC BY-SA 3.0) and barbed wire (Chairman of the Joint Chiefs of Staff / Flickr).



