When Dutch authorities apprehended a team of Russian hackers, it became clear that Vladimir Putin is willing to send teams of cyber operatives abroad. How much damage could they do in a state like Florida? We asked the experts.
Florida, the home of hanging chads and other election vulnerabilities, may be on the brink of another problem: the WiFi Pineapple NANO — a tool designed to audit or hack WiFi networks.
The equipment was discovered by Dutch police after they detained four hackers, who turned out to be Russian special agents plotting to infiltrate the Organization for the Prohibition of Chemical Weapons.
Although these agents were caught and identified, it is the technology that could threaten Florida. Election security experts believe the Pineapple could hack, and potentially alter, election results in the Sunshine State.
Cellular modems, connected to voting machines, are used to transmit election results wirelessly to the election department. The modem becomes a WiFi hotspot. When the Pineapple is active, it can connect to the cellular modem that is transmitting election results to the election department.
“There is no unhackable system in the world. There will be no unhackable system — not in banking, not in elections, not anywhere else.”
“Pineapple has the capability to run a fully automated attack against [wireless voting machines],” Harri Hursti, an expert on the vulnerability of election systems, told WhoWhatWhy.
Hursti pulled off the so-called “Hursti Hack” of a Diebold optical-scan voting machine in 2005 and is a co-author of the recent DEF CON hacking conference report on “Cyber vulnerabilities in US election equipment, databases, and infrastructure.” Anything that connects wirelessly is potentially vulnerable to a Pineapple hack. That includes mobile devices, which would also include all voting machines such as the ones used in Florida that transmit data using cellular modems.
“Pineapple can go after all of those,” Hursti said. “When you look [at] election offices and election HQs, Pineapple always finds a target-rich environment in those.”
It’s all a bit technical, not surprisingly. Here’s how it works:
Like many states, Florida puts paper ballots through digital-scanner voting machines, such as the DS200, manufactured by Election Systems & Software (ES&S). All counties in Florida are using digital-scanner machines certified by the US Election Assistance Commission (EAC). These voting machines count the ballot and save a digital image to an internal cellular modem, such as the Verizon C2 wireless modem, authorized by the state.

Employees at the Hillsborough County Supervisor of Elections office feed test ballots into the DS200 Tabulator which reads the ballots during a logic and accuracy test Tuesday, Aug. 7, 2018 in preparation for the midterm elections. Photo credit: © James Borchuck/Tampa Bay Times via ZUMA Wire
The modem then transmits the data via the internet to an election management system at the county election department. A “poll tape” with tabulated results is also produced by the voting machine. Experts agree insecure transmission of voting data over the internet is the fatal flaw of these voting machines.
“It goes back to how these cellular modems are implemented,” said Matthew Bernhard, a computer science Ph.D. student at the University of Michigan, who recently testified as an expert in a trial on the security of voting machines in Georgia.
“If they are not implemented the way that the vendors claim they are, you know, there’s a mistake, [then] it’s certainly possible that someone sitting in Russia could infect voting machines in the United States,” he added.
Hacking From a Parking Lot
.
Florida Secretary of State Ken Detzner (R) tested and certified the use of wireless voter machines in all 67 county supervisor of elections offices back in 2015.
An active Pineapple simply needs to be brought to the parking lot of a polling site to begin hacking wireless voting machines, according to Hursti.
When the Pineapple is in range, it can trick a cellular modem in a voting machine to connect to it rather than its intended destination. Hursti said the Pineapple can collect information through WiFi, Bluetooth, radio, and software-defined radio (SDR).
With the right programs, Hursti added, “Pineapple [can] do anything from reading airplane communication beacons, to analyzing any radio signals on almost any frequency, to [using] software to get mobile phone network control data from the towers.”
Related: Hackers Eviscerate Election Tech Security… Who’s Surprised?
Related: Voting Machine Company Admits Installing Vulnerable Remote-Access Software
#AMA: "I'm Harri Hursti, voting machine hacker and election security expert"
💬: u/HarriHursti on https://t.co/kCqHM6fCjm pic.twitter.com/3Z6O5NGJCH
— Reddit (@Reddit) November 1, 2016
The problem, Bernhard pointed out, is that most election machine vendors don’t implement strong code or cryptography in their machines.
“Coupled with the fact that now they’re transmitting election item results with a cellular modem and relying on just ballot images for audits, it is kind of a recipe for disaster if you ask me,” Bernhard said.
But Florida Department of State spokespersons claim voting machines are safe.
Tricks and Traps
.
“Voting machines are not connected to the internet,” Sarah Revell said in a McClatchy article, adding that “it is important to note that when transmitting election data everything is encrypted and authenticated.”
Hursti said the statement itself is “a kind of trap.”
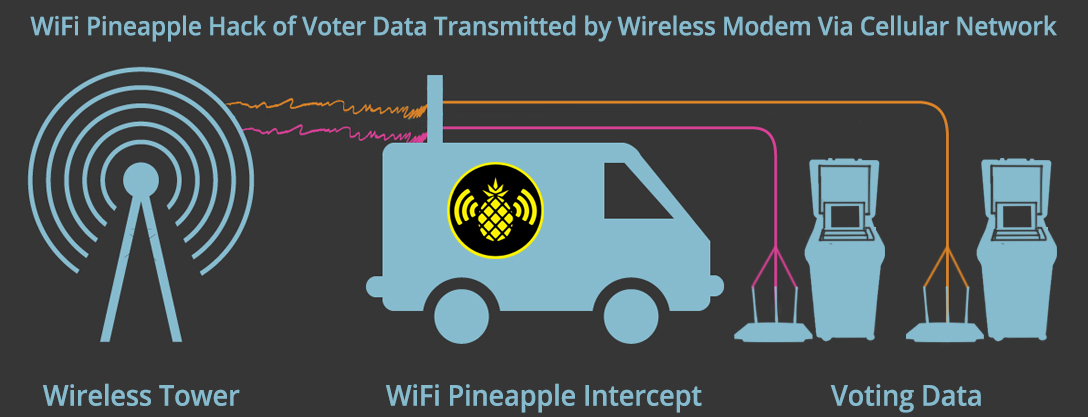
Photo credit: Adapted by WhoWhatWhy from EFF / Wikimedia (CC BY 3.0), GTorres / pixabay (CC0 1.0), Gregbaker / Wikimedia (CC BY-SA 4.0, and hatalar205 / Wikimedia.
Verizon, AT&T, and all cell-service providers are using the internet. Again, smartphones or cellular modems all connect to the internet now. All internet users at home or roaming are accessing the internet via an IP network, and that is where a hacker using devices like a Pineapple will trick a voting machine or a personal device to connect and share private information.
Even when election officials run software and collect election results using IP networks known as virtual private networks (VPNs) — which essentially create a private network over the public internet — it’s not completely isolated or private, Hursti said. These VPNs can be breached with the right tools — the tools found with the Russian hackers detained in the Netherlands this year.
The claim that the transmissions are authenticated and encrypted, according to Hursti, doesn’t change the fact that the data is still traveling over public internet infrastructure. And, if modern voting machines use cellular modems to transmit data, then that data can be breached, even if the modem is connected to a private network.
“It would not be easy but certainly plausible that a nation state like Russia could either be disrupting the transmission of election-night results or directly affecting the actual voting machines and disrupt[ing] an election,” Bernhard said.
Bernhard further explained that digital ballot images — like any file saved on a computer — can be edited.
Related: Activists Concerned About Counties Destroying Ballot Images
“They could destroy paper ballot images,” Bernhard said. “They could alter paper ballot images … An image is just another file that’s on the computer, and it’s not that hard to go in and edit it. If it’s an image of a ballot, to make it look like it was a vote for someone else.”
Hacking From Afar
.
Both Bernhard and Hursti also agree it’s possible to hack voting machines from overseas.
Hursti looked at Signaling System No. 7 (SS7) as an acute vulnerability whereby hackers could connect to cellular modems around the world and audit information without anyone knowing it was happening.
SS7 is a telecommunications standard that is integral to connecting and disconnecting phone calls, making toll-free calls, billing, and wireless services among others. It was designed in the pre-digital 1970s and has since evolved to work in the digital world. Now, all mobile networks route their calls through SS7, Hursti explained.
SS7 represents another weak link in any system that transmits info using WiFi — like cellular modems in voting machines. A cellular modem is itself a WiFi hotspot.
By exploiting SS7, hackers can eavesdrop on calls and essentially track a cell phone user. They can also steal information transmitted from a cellular modem in a voting machine. Hursti said. Once a modem is using a mobile network (i.e., the internet) it is just like any other mobile device vulnerable to an SS7 attack.
Did you know…
DS200 machines can be found at all Early Voting and Election Day polling places. A DS200 is a digital voting machine that uses paper ballots to receive cast votes.
For more information:
Call us at (954) 357-7050
Visit our website: https://t.co/UtnmGnOfS3 pic.twitter.com/mvguSzSkbC— Broward SOE (@BrowardVotes) August 23, 2018
If you have the phone numbers or any important numbers needed to connect, Hursti says, there are commercial companies around the world that will sell anyone the service to hijack a call, “routing it through them” and then passing it along to the intended recipient without the caller becoming aware of the hack.
“There will be a little bit more delay,” Hursti said. “And that delay will be the only telltale that something might be going on.” The same would be true with voting information transmitted via a cellular modem.

Bernhard said most voting machines are not being evaluated by any entity other than the vendors. ES&S, the main vendor of wireless voting machines in Florida, has been known to keep manuals and other product information tightly sealed.
Related: Voting Machine Vendor Threatens Election Transparency Group
“We’re starting to see that change, I hope,” Bernhard said. “Until we know that, it’s hard to be confident that they are implementing all these complicated things that they’re saying they are.”
Hursti compared election offices to IT departments that just happen to run elections, and he said the precincts are not currently robust enough in the US. Even with encryption, they are not safe from the auditing tools Russian hackers have been caught red-handed with.
Related: We Don’t Know What Our Computers Are Doing
“There is no unhackable system in the world,” Hursti said. “There will be no unhackable system — not in banking, not in elections, not anywhere else. You have to have a secondary system that makes sure, if things get hacked, you capture that and are able to mitigate it … You have to verify the results.”