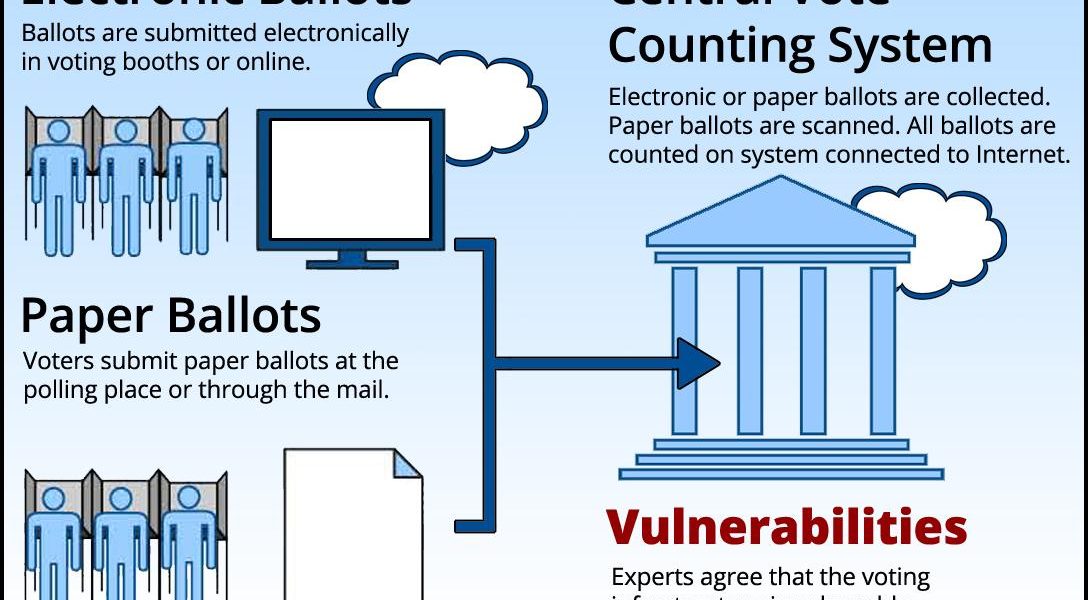
When people think of election theft, many assume that means individuals taking measures up to and including the moment that votes are cast. However, experts agree that thanks to the increasing reliance on electronic voting and vote-counting, the very infrastructure itself is also vulnerable — to attacks from the outside. This could include foreign powers pursuing their own agenda.
What if a foreign head of state had the power to handpick our next President? It sounds like the plot of a movie, but it actually might be in the realm of possibility.
Most people take our elections for granted. The few who don’t often suspect that one party might be trying to steal votes from the other. But they don’t envision that the theft could be coming from outside US borders.
What experts are telling us, though, is that our voting machines are so insecure that all elections, whether at the national, state, or local level, are vulnerable to being attacked by hackers in other countries.
Chinese and Russian hackers, for instance, have reportedly breached government databases. The government of Israel has been accused of espionage against the US and of hacking in France. And tech giants like Google and Sony have been attacked successfully in the past. Indeed, it’s been proven that everything from cars to sniper rifles to traffic lights can be broken into.
Certainly there would be a massive interest abroad in manipulating US elections.
For example, Russia may want to prevent a hawk like John McCain, who wants weapons in the Ukraine and faces a tough battle for his job next fall, from getting reelected.
Israel’s leaders believe that the Iran nuclear deal would doom their country, so if they thought they could get away with it, would they try to put in office US representatives who share that view?
And if China wanted to undermine trade deals like the Trans-Pacific Partnership (TPP), the Trade in Services Agreement (TiSA), and the Transatlantic Trade and Investment Partnership (TTIP), which are seen by some as attempts by the United States to encircle and maintain dominance over that emerging Asian power, it could swing elections for legislators who have come out against such trade pacts.
This begs the question: Given that the security at some of our most protected institutions can be breached, and given that US elections pose an enticing target for our adversaries, what would prevent a foreign agent from hacking our ballot boxes?
The answer: Not much.
Experts indicate that the election systems in place today do not provide the adequate protection that would be able to stop a foreign hacker — a hacker anywhere, in fact — from rigging our races. Even worse, these attacks could go undetected.
It’s difficult for computer scientists to pinpoint exactly how many programmers around the world are capable of remotely breaching an election software — whether that’s the vote itself or other related data — like voter registration records. However, many agree that the intellectual barrier is not significant.
Since such attacks can easily go unnoticed, evidence of remote hacks is scarce. But it’s likely they’re happening more than we know, considering that unencrypted connections over the open internet aren’t too hard for a knowledgeable college student to breach.
Thus, it’s conceivable that anyone around the world with a somewhat advanced knowledge of computers is able to peer into our electoral machinery and potentially compromise our votes.
Weaknesses in Internet Voting
Each state conducts its own system of voting, and some election protocols are more secure than others. That said, all modes of computerized voting are subject to being compromised.
Take internet voting, also known as iVoting, which allows citizens to vote through an online portal or by e-mail or by fax. If not encrypted properly, these transactions could be compromised.
Jonathan Katz, Director of the Maryland Cybersecurity Center at the University of Maryland, College Park, observes that even if a system appears safe, voting online allows hackers to examine the system for points of vulnerability.
“I wouldn’t necessarily go so far to say that everything done over the internet is insecure, but you are certainly opening yourself up to the potential for hackers to look at your system and try to find vulnerabilities,” Katz told WhoWhatWhy.
Since 2000, numerous computer and voting experts, including the National Science Foundation, have authored studies warning about the serious vulnerabilities of iVoting. Some of these studies cite unsuccessful internet voting systems that have been implemented in such countries as Estonia, France, and Norway.
One report, produced by computer scientists at the request of the Pentagon, examined a pilot iVoting project and concluded that an internet- and PC-based voting system presented “fundamental security problems” that couldn’t be fixed without a “radical breakthrough.”
Cyber attacks, the report concluded, “could occur on a large scale, and could be launched by anyone from a disaffected lone individual to a well-financed enemy agency outside the reach of U.S. law.”
Thus, the pilot program in question was cancelled. Yet various forms of iVoting remain in place in over 30 states, despite its vulnerabilities.
Weaknesses in Electronic Voting
Even electronic voting, or eVoting, in which the machines are ostensibly not connected to the worldwide web, poses significant risks to an election’s integrity.
Some states use direct recording electronics (DREs), wherein voters use a push-button or touchscreen machine to directly record their choices. The votes are then recorded on some sort of media, then tallied later. Other states use optical scan equipment, in lieu of hand counting, to scan and total the paper ballots. (Check to see what equipment is used at your polling place.)
Despite its seemingly safe appearance, there are subtle ways the eVoting process could be susceptible to attack. For, in many cases, these systems actually do connect online.
John Sebes, CTO of the Open Source Elections Technology Foundation (OSET), told WhoWhatWhy that the most significant logistical issue for local officials is something called the election management system, or EMS.
As a component of the overall apparatus, the EMS is used for election data management and data entry — most likely on a PC in an elections office. Sebes said that, in theory, EMSs are never supposed to be online, but sometimes they get connected anyway. Not only do hackers then have the potential to breach election data on the PC, but malware could affect the removable media when it is taken out of the PC and inserted into the voting machines.
“Anytime you have a breakdown of safe computing around a workstation that’s running an EMS, that’s a really significant threat,” contended Sebes. The risk is multiplied, he said, when these systems run on old versions of Windows, which have significant vulnerabilities.
Sometimes vendors will send software updates to patch a machine through an EMS via the internet. Other times vendors can directly update their machines through a dial-up connection. Once votes are cast, electronic ballots can be sent via an online connection to central tabulators that tally the results. Since all of these transactions involve the internet, the same threats that apply to iVoting also apply here .
Maryland Cybersecurity Center’s Katz noted that if one part of a system is vulnerable and has unsecured connections, hackers who gain access to its inner workings could open up elections to cyber attacks.
“I think that the big problem here is this: It’s not just about devising a secure protocol,” Katz said. “It’s about making sure that the entire ecosystem of all of parts that have to work together are all secure. And that seems right now to be very difficult to do.”
In addition, vulnerabilities in the “ecosystem” are not limited to internet-related issues. The range of problems includes weak passwords, physical insecurity of the machines, and inadequate post-election audits.
Though “it seems kind of far-fetched,” Sebes observed, to think that “significant state-sponsored adversaries who are busy pillaging personnel databases of federal and large data organizations would bother to do a similarly targeted attack on a locality that accidentally had an EMS connected to the internet,” nonetheless such an attack cannot be ruled out. “As we’ve seen in the past couple months,” he said, “it’s really hard to assess the likelihood of attack from really sophisticated adversaries.”
And without a paper trail (as is the case with some DREs), there is no way of knowing an attack ever took place.
The Vendors
What about the track records of the voting vendors that are running our elections? How are they trying to mitigate these threats and how do they stack up next to the security of other organizations — the US Department of Defense or Microsoft Corp., for example?
They don’t.
According to Greg Miller, chair of the OSET Foundation, both the software and the machines used by these vendors are massively outdated.
“By and large, the hardware that’s been relied upon since 2005 for these voting systems is just no longer made,” he said.
Similarly, noted Miller, the software that runs on many of these machines is no longer supported. Moreover, some software upgrades are not even possible on the outdated hardware, which do not have capacity to run the advanced programs.
Despite continuous warnings from experts about election insecurities, officials still rely on vendors that refuse to disclose how their machines run, deeming their code “proprietary.”
The three largest voting vendors in the United States — Electronic Systems & Software, Dominion Voting Systems, and Hart Intercivic — did not respond to requests for comment.
The Alternative
“If you can breach Pentagon security, you’re clearly going to be able to breach internet voting security,” election activist Bob Fitrakis told WhoWhatWhy. “It seems like an obvious way in which to influence American politics. I think the logical thing is to go back to paper ballots, which most of the democratic world use, and count them at the precincts. That’s probably what needs to be done more than anything.”
In recent years, computer scientists, activists, whistleblowers and privacy experts have been calling for an end to the election status quo. They contend that hackers all over the world pose a significant threat to the integrity of our ballots and that this flimsy system creates the context for the mounting evidence of election fraud that has been uncovered.
The legitimacy of the US political process rests squarely on these machines. Even if manipulation by foreign agents were not happening today (and we would have little way of knowing if it were), just the threat of hacking should be cause for deep concern. And that’s not even taking into account the possibility that foreign and domestic agents alike could be physically breaching the voting systems — something even easier than a remote hack.
“This is a national security issue, because it is an issue of fundamental rights that goes to our human security,” said Joe W. “Chip” Pitts III, a lecturer at Stanford Law School. “If that infrastructure of freedom and democracy is not secure, none of us are secure.”
Related front page panorama photo credit: Voters (Maryland GovPics / Flickr), Laptop user (Indi Samarajiva / Flickr), Vote by mail (Marlon E / Flickr)