New Cyber-Weapon Belies Spy Agencies’ National Security Claims
Washington’s cyber-spies haven’t been resting on their laurels. Computer security researchers have uncovered a powerful new malware built for spying. And its targets are far from the usual national security threats that intelligence agencies say they need to watch.

Washington’s cyber spies haven’t been resting on their laurels since unleashing the infamous Stuxnet computer worm in 2009.
Now, researchers at security firm Symantec have exposed another advanced cyber-weapon called Regin, which British and American intelligence agencies very likely used to hack into computer systems at the European Union, along with other high-level targets around the world.
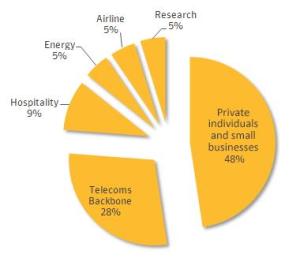
The global Regin “hit list” belies the intelligence agencies’ claims that their spying is limited to missions of national security. Nearly half of those targeted were private individuals and small businesses, according to Symantec. The other half included telecom providers, energy companies, airlines, research institutes and the hospitality industry.
The discovery of the program, which takes over entire networks, came just days before the United Nations adopted a major resolution condemning unlawful and arbitrary government surveillance. The document calls on states to align their surveillance practices with international human rights law, make the frameworks under which they operate publicly accessible and provide victims with opportunities for redress.
And who lobbied hard and unsuccessfully to weaken the resolution’s language? The United States and its “Five Eyes” spying alliance, which includes the U.K., Canada, Australia and New Zealand. Demonstrating just how resistant those nations are to limits on cyber-spying, the Five Eyes argued against provisions in the U.N. statement that called for an end to indiscriminate electronic surveillance.
It’s little wonder, when you understand how powerful the Regin malware is. It is so sophisticated that researchers concluded it could only have been created by nation states. It disguises itself as common Microsoft software while stealing data from infected computers, and deploys its payloads in stages to avoid detection.
Built for Spying
Symantec’s researchers call it a “top tier espionage tool” on par with Stuxnet, the U.S.-Israeli virus responsible for sabotaging nuclear centrifuges at Iran’s Natanz facility in 2009. That malware exploited unpublished vulnerabilities, called “0days,” in Microsoft’s Windows operating system, which allowed it to infect thousands of machines in over 100 countries around the world over.
But upon dissecting its code, researchers found Stuxnet’s’ mission was narrowly targeted at industrial control systems like the kind running inside Iran’s nuclear facility. Even then, the virus reportedly had to be physically implanted via USB sticks by Israeli double agents, believed to have been recruited from the Iranian dissident group Mujahedeen-e-Khalq (MEK).
But while Stuxnet was a tool of sabotage, Regin was explicitly designed for spying.
Last year, documents obtained from Snowden revealed “Operation Socialist,” a top-secret hacking mission undertaken in 2010 by NSA’s British partner GCHQ. The agency successfully infiltrated the computer networks of the Belgian phone and Internet provider Belgacom by tricking its engineers into clicking on a fake LinkedIn page. That gave British spies access to the company’s data, as well as the ability to spy on Belgian Internet customers, which include the European Commission, the European Parliament, and the European Council.[1] In a separate report, it was revealed that the NSA was also targeting the communications of EU officials.
Antivirus vendors aren’t pointing fingers, but industry sources familiar with the investigations are convinced Regin was the malware found on Belgacom and EU computers following the attacks, linking it back to U.S. and U.K. intelligence agencies.
The giveaway — according to Ronald Prins of Fox IT, the company hired to investigate the Belgacom hack — is UNITEDRAKE and STRAITBIZARRE, tools previously disclosed as part of the NSA’s computer hacking arsenal that match the functionality of components found in Regin. Both are described in top secret documents as tools for installing and managing “implants,” which are essentially bugs that allow spies to remotely monitor and control the machines they’re placed on.
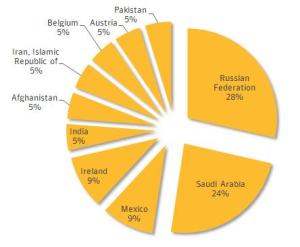
Symantec’s report says that Regin has probably been active since at least 2008, but researchers say some components have timestamps dating as far back as 2003. More than half of the malware’s victims appear to reside inside Russia and Saudi Arabia, but it has also been aimed at Mexico, Ireland, Belgium, Austria, India, Pakistan, and others. Notably absent from the list: the United States and its Five Eyes surveillance allies.
Even security researchers are targets. The security firm Kaspersky Lab identified one Regin victim as cryptography professor Jean-Jacques Quisquater, who, just like Belgacom and the EU, was previously reported as one of the individuals targeted and compromised in the U.S. and U.K. attacks.
Of course, this is not the first time the U.S. and U.K. have been linked to economic and political espionage. Early Snowden files revealed that the NSA had targeted Petrobras, a state-owned oil company in Brazil. Other revelations showed the agencies eavesdropping on German Chancellor Angela Merkel, former Israeli Prime Minister Ehud Olmert, and even charities such as UNICEF.
[box] WhoWhatWhy plans to continue doing this kind of groundbreaking original reporting. You can count on us. Can we count on you? What we do is only possible with your support.
Please click here to donate; it’s tax deductible. And it packs a punch.[/box]