What exactly, for example, does someone mean when they say “voter fraud?” And does it mean what they think it means?
|
Listen To This Story
|
With control of Congress still in the balance on the morning after the midterm election and many races decided by thin margins or still too close to call, the coming days will be filled with recounts, legal challenges, and experts (or so-called experts) providing their analysis and legal takes. To help you keep up and understand who knows what they are talking about, we have compiled a list of the most important election-related terms that you need to know.
Elections are a complex enterprise and some of the summaries presented here barely scratch the surface. But all should make it easier to follow a discussion or debate, spot lies small and big, and point you in the right direction if you wish to probe deeper.
Election Integrity (or EI) — The degree to which elections earn and warrant, as opposed to simply assume or demand, the trust of the public. It also refers to the movement, or collective efforts, to bring security and transparency to the electoral process, including both its vote-casting and vote-counting components. Because the term “election integrity” has also been weaponized by the far right and white supremacists to promote targeted disenfranchisement and a racially restricted electorate, Election Transparency is preferred by some to describe the advocacy of public, observable vote counting and similar reforms.
Election Forensics — The examination (primarily) of data patterns for anomalies and disparities that may be indicative of vote mistabulation, whether resulting from error or fraud. More broadly, it refers to the general study of the conduct of an election to assess whether it has been free and fair and a more or less accurate translation of the public will into electoral results. Because “hard” evidence — such as memory cards, code, machine hardware, and voter-marked ballots — are rarely available for examination, forensic investigation of election results almost always depends on statistical analysis and inference. Analytic approaches may differ markedly in probative value; virtually all of the “forensic” claims advanced by Donald Trump’s “Stop the Steal” campaign have been thoroughly debunked.
Red Shift — A disparity between computerized vote counts and other measures of voter intent, such as exit polls, tracking polls, or hand counts. The shift is “red” when the vote-count disparity favors the more right-wing candidate (or position). If, for example, the unadjusted exit poll result for an election was 52%D/45%R (D+7) and the official vote count was 49%D/50%R (R+1), the red shift would be 8 percent. A “blue shift,” which has occurred extremely rarely, would refer to a disparity in the opposite direction. Note that red (or blue) shifts may or may not change the winner.
Margin of Error — MOE refers to the expected variance of any sample of a larger whole with respect to a particular characteristic. In polling, that characteristic is often voting preference, though it might be approval/disapproval or some other opinion. It is important to understand that MOE is a strictly mathematical calculation that presumes perfect randomness of the sample in question (e.g., white and black marbles picked by a blindfolded person out of a box that has been thoroughly shaken). It is expressed as a range in which we expect the sample to fall, generally (though not necessarily) 95 percent of the time. It does not consider aspects of sampling design or execution that introduce non-random factors.

Total Survey Error — TSE is an expansion of MOE that considers aspects of sampling design or execution that introduce non-random factors. Such factors might be the “cluster” sampling that is typical in exit polling (discrete precincts are sampled rather than a random selection of voters from an entire jurisdiction), as well as anticipated or measured selection and/or response biases. As these factors can be difficult to quantify, TSE is generally a somewhat less precise, though potentially more useful, parameter than is MOE. MOE never exceeds TSE.
Tracking Polls — Candidate-preference polls taken prior to an election that often also include such metrics as job-approval ratings. Polling aggregators such as FiveThiryEight combine, weight, and average tracking polls to present a less noisy, more reliable indicator of voter preference and opinion.
Selection and Response Biases — Selection bias refers to non-random factors introduced, wittingly or unwittingly, in the process of selecting respondents for a sample. An example would be an interviewer consciously or unconsciously avoiding approaching the nth respondent, identified by the random sampling protocol, because of some aversion to the person’s appearance, behavior, or apparent political affiliation. Response bias refers to the greater or lesser tendency of certain groups (e.g., age, race, gender, political affiliation) to participate when selected for a survey. The red shift in 21st century US elections has been reflexively attributed to response bias (i.e., greater reluctance to participate) among Republican voters.
Likely Voter Cutoff Model — A poll sampling methodology modification, introduced by pollsters several years after the start of the computerized vote counting era, that screens out all but likely voters from polling samples. Since some less-likely voters, who get excluded, wind up casting a vote, the LVCM is a significant sampling distortion. And since the screening questions cover such factors as stability of residence and prior frequency of voting, the LVCM disproportionately eliminates more left-leaning respondents (students, transients, renters, young voters, urban voters) from the sample, and thus skews it right. The LVCM should fail if votes are counted as cast — it has generally succeeded.
Exit Polls — Surveys taken of voters as they leave polling places after voting. In addition to “Who did you vote for today?” questions, a substantial amount of demographic and political opinion information is generally gathered. Voters fill out questionnaires anonymously. Because much voting now takes place prior to Election Day and by mail, exit polling now also surveys voters remotely. The exit poll sample will generally have several non-random aspects; the pollster (primarily Edison Research in the US) uses data-rich models to weight samples to reflect the anticipated demographic composition of the electorate. Although exit polls in the US tend to be controversial when used as baselines for vote-count verification, they often provide the earliest and often virtually the only data indicative of possible inaccuracies in the official count. They are used routinely for verification and fraud-detection purposes in the elections of countries other than the United States.
Exit Poll Adjustment — The process by which exit poll percentages are brought into virtual congruence with vote count percentages as vote counts become available on election night. Although the process is algorithmic and fairly complex, it essentially consists of a forced reweighting of the exit poll responses with the “Who did you vote for?” question overriding all others. Thus, if the unadjusted exit poll underrepresented votes for Candidate A (relative to the official vote count) by 5 percent, every question on every questionnaire indicating a vote for “A” will be upweighted accordingly. Thus, if a respondent who indicated a vote for “A” also indicated she identifies as a Republican, she will now count as 1.05 of a Republican voter and the apparent proportion of “Republicans” in the sample will increase commensurately.

Unadjusted Exit Poll — A weighted exit poll in which the vote counts for the election being polled do not factor into the weighting. That is, the poll results are not “contaminated” by vote count data and provide our best (if imperfect) forensic baseline for vote count validation. Election forensics analysts generally regard the first publicly posted exit poll results — often within a minute or so of poll closing in a state (though it can be an hour later in “double-time-zone” states) — as “unadjusted,” though we would not know for sure whether any adjustment (always toward congruity with vote count percentages) had occurred prior to first public posting.
Pre-Set Vote Count Manipulation (i.e., Rigging) — Vote count manipulations deployed into equipment code (e.g., memory cards) some time (often more than a month) in advance of the equipment’s use in an election. Such rigs, although comparatively easy to install, would necessarily be calibrated in advance and are susceptible to late movement in electoral dynamics, which might cause them to fail in their purpose of altering the winner.
Real-Time Vote Count Manipulation — Refers to manipulation of vote counts during the voting or counting phase of an election. Most frequently a “man-in-the-middle” exploit, such rigs require the deployment of significantly more infrastructure than the pre-set variety, but are more flexible, allowing real-time calibration of the magnitude and distribution of the interference. Online voting would be particularly susceptible to this type of manipulation.
Baseline — Any data set that serves as a control or norm against which a particular data set can be measured. The baseline can be contemporaneous (a national poll might serve as a baseline against which battleground state polls, and their disparities, can be measured) or temporal (for example, a sequence of previous contests from which the contest to be analyzed departs in some significant way). Baselines are critical to the work of statistical forensics analysts.
Second-Order Comparative — A statistical forensics analysis that relies on a secondary baseline to assess the potential causes of red-flag anomalies or disparities. Best explained by example: Looking at the disparities between vote count(s) and exit poll(s) in a single contest or some set of contests would be a first-order comparative; comparing two discrete subsets of vote count/exit poll disparities, one consisting of non-competitive contests and the other consisting of competitive contests, would be a second-order comparative. Other comparisons might be: Swing states versus national aggregate; one party’s versus another party’s primaries; hand-count versus computer-count jurisdictions; contests counted by one type or brand or equipment versus a different type or brand; etc. The probative value of second-order comparatives, where a “disparity of disparities” is found, is often much greater than that of first-order comparatives. Such comparatives raise the question of whether any factor other than the targeting of one set of contests can plausibly explain the difference.
CVS Analysis — Cumulative Vote Share analysis (also known as Cumulative Vote Tally — CVT) refers to a statistical forensics approach that orders precincts or counties by increasing (or decreasing) size within a larger jurisdiction by size and looks for unexpected patterns of candidate cumulative vote share. The Law of Large Numbers predicts cumulative vote share curves that flatten to near-flat lines as precinct/county size increases. When we instead find sloping lines, it raises the question of why vote share correlates with precinct/county size. While there may be benign explanations for such correlation, one red-flag explanation to consider is that manipulators have targeted larger precincts/counties where the shift of a given number of votes will be less noticeable.
Fraction Magic — A term coined by election transparency advocates Bev Harris and Bennie Smith to refer to the fractionalization of votes, which are encoded as decimal (e.g., 0.54, 1.27) rather than integral (e.g., 1) values. An unknown percentage of voting equipment currently in use is fraction-capable. Although only very rarely needed (e.g., elections in which votes are proportioned to acres of land owned), fraction capability can greatly facilitate vote count manipulation and make precision-calibrated, real-time rigging feasible without elaborate infrastructure.
Help America Vote Act — HAVA was federal legislation passed in 2002 that greatly accelerated the full computerization of US elections. It used carrots (funding) and sticks (mandates) to push states into touchscreen voting (DREs) and was entirely lacking in cybersecurity provisions to protect the increasingly concealed process it promoted. Authored by leading Republicans, including Sen. Mitch McConnell (R-KY), HAVA was sold to naïve Democrats as a means of increasing turnout — a red flag, as the GOP had long been on a mission to reduce turnout to its advantage.
HCPB — Acronym for Hand-Counted Paper Ballots, ballots cast on paper and counted in public by humans (counting teams to generally include representatives of each major party and a non-party-affiliated member).
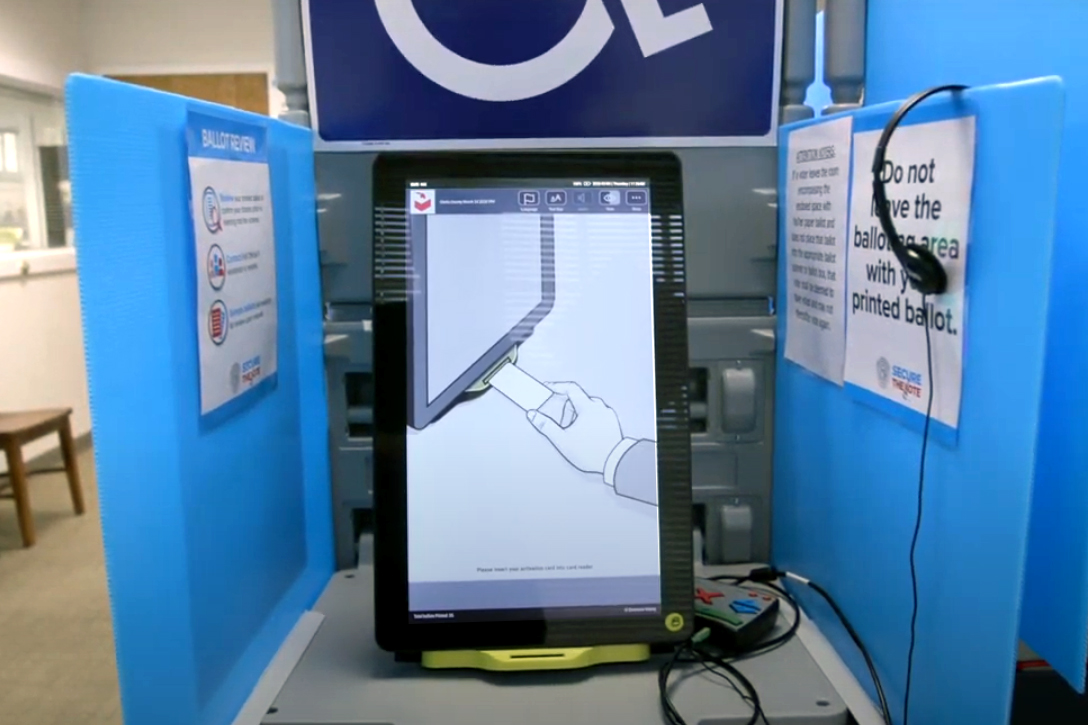
HMPB — Acronym for Hand-Marked Paper Ballots, ballots marked by the voter’s hand rather than by a mechanized or computerized device. The distinction is crucial, as ballot-marking devices (BMDs) introduce new and powerful fraud vectors, and the call for “paper” or “paper ballots” has frequently come to dress up in faux integrity a shift from pure touchscreens (DREs) to barcode or QR-code BMDs, which are equally inviting to digital fraud.
Equipment Vendors — The manufacturers, distributors, and often programmers of the equipment used for voting, vote counting, and vote count reporting. Principals are currently Election Systems and Software (ES&S), Dominion Voting, Hart Intercivic, and Scytl. At one time, Diebold, which became Premier, had a major share of the equipment market. Regional subcontractors — such as Triad, VR Systems, Command Central, LHS, and Kennesaw State University’s Election Center — program, distribute, and service the equipment. Most of these manufacturers and vendors have ties to the political right.
DRE — Direct Recording Electronic voting machine, also known as a “touchscreen.” DREs can be paperless or fitted with a “paper trail” printout, generally similar to a gas station receipt roll. The voter can, in theory, check his or her vote, though the programmer can easily code the DRE to print a vote for “A” while recording a vote for “B”. Recounting or auditing the paper trail, where available, tends to be difficult if not impossible, as the roll frequently jams, causing incomplete recording, and is in any event hard to read and not at all durable.
BMD — Ballot-Marking Device refers to programmable equipment that takes the place of the voter’s hand in creating or marking his or her ballot. Originally designed to assist disabled voters, BMDs have been adopted in most states and counties for general use. The voter usually indicates each choice on a touchscreen, with the program transforming that choice into a machine-marked paper ballot.
Barcode (or QR Code) BMD — A BMD that, rather than printing checks or Xs onto an ordinary ballot template, instead encodes the voter’s choices (and possibly other information) in a barcode or QR code readable only by a scanner (often only a proprietary scanner). As the voter cannot read the barcode, which is the official ballot of record, a “summary card” is sometimes provided to the voter indicating his or her choices. Such summaries have been problematic as they are difficult to read and, when tested, voters only rarely catch errors and omissions. According to their inventor, risk-limiting audits are not capable of auditing or verifying the process by which the BMD translates voter intent into an official vote.
Permission to Cheat — A term coined to describe a species of “hybrid” BMD that gives voters the option to waive verification of whether their ballot summary card accurately reflects their intent before the ballot makes its final pass under the print heads, thereby allowing the programmer to alter, risk-free, only the subset of votes that the computer “knows” will not be verified. In effect, the computer makes the voter “play first,” so it can cheat with impunity.
Risk-Limiting Audit — A kind of audit that, instead of drawing a flat (e.g., 2 percent) sample of ballots, instead samples each audited contest in a progressive manner until a set level of confidence is reached that the correct winner has been identified by the initial count of votes. An RLA can result in a full (100 percent) audit if that level of confidence is not achieved, which would be because of computerized counting error or fraud sufficient to alter the apparent winner. The advantage of RLAs is that for elections that are not close only a small sample of ballots is needed for verification of the winner. Where elections are very close, however, a large sample, bordering on a full “recount,” is needed and the protocol is rather slow and clunky. RLAs have now been adopted by a handful of states, though in some cases only as pilot programs.
Digital Ballot Image — DBI refers to images of cast ballots created by ballot scanners enabled with such capacity. Each ballot becomes, in essence, a discrete file (e.g., PDF or JPG) that is stored and can be reviewed for audit or recount purposes. This feature is generally optional: an on/off switch on the computer, set by election administrators, determines when the created DBI is preserved or instead destroyed within milliseconds of creation. Certain DREs can also create a voted-on digitized template that is in many respects the equivalent of a DBI. With demands for post-election verification having heightened dramatically in the wake of the 2020 election, and with hand counting boding to be problematic in a hyper-polarized and hostile environment, DBIs hold promise, in the eyes of many election transparency advocates, as enabling a more practical and less confrontational post-election verification process.
Modem-Equipped — When a given piece of voting equipment is networkable; that is, equipped with a modem and capable of outputting and inputting data or programming code via the internet. Such equipment, of which much more exists than was long acknowledged, is of course more vulnerable to interference by hackers.
Internet Voting — Also known as online voting, refers to remote voting via the internet. It is already an option in most states for a small sub-group of absentee voters, primarily military; but experts have warned that it cannot be made secure with current or foreseeable technologies. It is effectively unauditable, unrecountable, and unverifiable — open to both hacking and malicious programming. It is a seductive but, from an election transparency standpoint, potentially catastrophic solution to the many problems currently besetting US elections.

Vote by Mail — VBM is a species of at-home voting (VAH), which refers to the casting of hand-marked paper ballots via US mail or drop boxes. No-excuse mail-in voting is an option in the majority of states, and the only option in four, where forensics have generally been favorable and voters pleased. Ballot trashing and stuffing are potential problems to be considered, along with weakening of secret-ballot protections. Urged by Democrats in light of social distancing’s potential impact on in-person voting in 2020, VBM has been opposed at national and most state levels by Republicans leery of expanding the electorate. Many red and GOP-controlled swing states have cut back on VBM and reduced the number and accessibility of drop boxes. When mode of voting becomes more strongly correlated with partisanship, it gives rise to bimodal patterns in the counting process, which have been (erroneously) seized upon as evidence of fraud.
Voter (or Vote) Suppression — Tactics and strategies, whether public or private, aimed at making the casting and counting of a vote more difficult or impossible. These tactics and strategies include such measures as requiring a difficult-to-obtain voter ID; shortening early voting periods; closing local polling places; eliminating or reducing the number of ballot drop boxes; slowing down postal distribution or delivery of mail-in ballots; disqualifying ballots on account of slight variation between their signature and the signature on record; deploying machines that inherently cause bottlenecks and long lines or are prone to breaking down; purging voting rolls of legitimate voters; and at-poll challenging of individual voters’ right to vote and forcing them onto provisional ballots. They often disproportionately target specific groups of voters identified by the suppressors as likely opponents. The past two years in particular have seen a flood of such efforts, purportedly aimed at combating “voter fraud” and heavily concentrated in states under Republican control.
Voter Fraud — Distinct from “election theft” or “vote counting fraud,” it is fraud allegedly committed by individual voters, such as voting illegally, voting in the wrong precinct, voting more than once, or impersonating another voter. Studies have shown it is exceedingly rare — if for no other reason than that it is a felony and the reward/risk ratio is abysmal (oddly, virtually all of the very, very few cases that have turned up have involved fraud for the benefit of Republican candidates). But that has not prevented Republican lawmakers from invoking the specter of millions of illegal voters as a pretext for the passage of discriminatory and suppressive voter ID laws and a variety of other measures aimed at selectively disenfranchising and reducing the numbers of opposing voters.
Voter ID Laws — Primarily laws requiring a voter to have a photo ID and/or signature-match ID to be able to cast a ballot. Such laws — passed mainly in red states, and originally templated by right-wing organization ALEC (American Legislative Exchange Council) — have been justified as necessary to counter a supposed epidemic of “voter fraud,” for the existence of which no evidence has been presented. The laws generally impose logistical burdens that strongly impact constituencies (e.g., urban, poor, minorities, nondrivers) identified by Republican strategists as adverse.
Provisional Ballot — A type of ballot, created initially under the Help America Vote Act (2002), that voters experiencing problems with registration, identification, or location are obliged to cast. Provisionals are generally the last ballots to be counted (they require a validation process), and are frequently rejected as invalid or not counted at all when it appears that they can’t alter the outcome of a given election.
Dark Money — Campaign funding, often from the mega-wealthy and corporations, that does not require sourcing to the donor. A series of primarily 5-to-4 party-line SCOTUS decisions over the past two decades found unlimited campaign expenditures with no sourcing to be constitutional, opening the floodgates to vast amounts of “dark money” pouring into US election campaigns.
Gerrymandering — The drawing of jurisdictional boundaries for partisan advantage. Practiced throughout US political history, gerrymandering has become an even more powerful political tool with the availability of “big data,” enabling more precise and effective boundary drawing. One result has been US House delegations — such as those in Ohio and North Carolina — in which, while the majority of votes statewide have been for Democratic candidates, the lion’s share of the states’ delegations have gone to Republican representatives. And the reverse is true in some Democrat-controlled states such as Maryland. Gerrymandered state legislatures have also distorted representation at the state level, and have had a recursive impact on the setting of laws and procedures governing the administration of elections. SCOTUS (5-to-4, party-line) in 2019 effectively gave a constitutional green light to gerrymandering for partisan advantage, leaving it to the legislatures to draw their own self-perpetuating districts. While a handful of states have instituted reforms entrusting the redistricting process to nonpartisan commissions, gerrymandering remains a highly potent political weapon that is often cited for individual and collective results favorable to one or another party, most frequently the GOP.
Elections, as I mentioned at the top, are complex affairs, and now probably more than at any time in living memory (at least) subject to great, and often hostile, contention. It pays to understand the vocabulary and the terms of the debate — what exactly, for example, someone means when they say “voter fraud” and whether such a term is being distorted or misapplied.
I hope the brief summaries above will prove helpful in sifting through the discourse, such as it is, and contributing your own observations.