Experts explain hand-marked ballots are required evidence in the face of mistrust and escalating violence among Trump supporters determined to avenge the former president’s loss.
Voting rights issues are in sharp focus as Congress considers two pivotal bills, the Freedom to Vote Act, and the John Lewis Voting Rights Act. In fact, the president said he will even consider an exception to the filibuster to get this national legislation passed.
Typically, conversations about voting rights focus on voter access to the ballot box. But this limited view overlooks the crucial next step — counting the votes. And here, both people on the right and left can agree: Our elections need to be safe, secure, and tamper-proof. Groups like the American Civil Liberties Union and Fair Fight are well known for protecting voters from unfair voting restrictions. Less known are the Coalition for Good Governance and Free Speech for People — two groups working to protect the votes themselves so that they can be accurately counted in a transparent and verifiable process.
Elections are run almost entirely on computers. Whether you mark a ballot by hand or vote on a touchscreen, nearly all votes nationwide are counted electronically. What’s less understood is that voting computers, like any computer, can be misprogrammed or hacked without detection, and thus require careful oversight. Both the Coalition for Good Governance and Free Speech for People are prying open the hood on these systems and working to make them both accurate and accountable to voters. Even just an accurate system isn’t enough; a stable democracy requires voters to understand the system is accurate.
The Battle Against the Touchscreen Is Hard to See
Though voting systems are federally certified, the certification standards allow for vulnerabilities like wireless modems. Plus states aren’t required to comply with federal security standards, permitting them to purchase any system they want. And even without these problems, the bottom line is no matter how strong a voting system’s defenses, an attacker can find a way in.
“Making a computer hack-proof is like building an unsinkable ship,” said Bennie Smith, a financial software developer turned election commissioner in Shelby County, TN. Smith discovered the computers in his Memphis precinct dropped votes by 40 percent. “Any system can be breached. You have to acknowledge that reality, and build safeguards.”
Coalition for Good Governance and Free Speech for People, are leading the only lawsuits to prevent ballot marking devices (BMDs) from subverting the votes of entire electorates.
Originally developed as assistive technology for voters who want help marking a ballot independently, BMDs are now marketed for all voters, completely replacing hand-marked ballots at the polls. But the device can be hacked to print the wrong votes.
“To accurately reflect the will of the voter, the process must include a reliable method to record voter choices, as the ground truth of voter intent,” said Susan Greenhalgh, senior adviser of Election Security at Free Speech for People. “Because computers are unreliable, we should narrow the use of BMDs for those who want their assistive features.”
Greenhalgh’s group has been fighting against insecure voting systems on a national and state level. Free Speech for People has challenged unsafe voting computers in South Carolina and Tennessee and is currently litigating against the insecure systems used in the highly populated Pennsylvania counties of Philadelphia and Northampton. In July, the group initiated a federal challenge, suing the Election Assistance Commission for meeting secretly and unlawfully with voting system vendors and subsequently weakening the federal voting system guidelines to allow wireless modems.
The group has also been pushing back against internet voting. In October they sent a letter, signed by other advocacy groups and over two dozen leading computer security experts, to the Senate Armed Services Committee advising against internet voting for soldiers and civilians living abroad. The letter cites extensive research stating that, among security experts, there’s “no debate” that sending ballots through the internet puts service members at “high risk” of disenfranchisement.
Coalition for Good Governance has been advocating for transparent vote counting in Georgia since 2017. That year, the group challenged the state’s old insecure voting system in an ongoing case that today challenges the new insecure system, which began roll-out in 2019. Recently, the court granted expert witness and renowned computer scientist Alex Halderman permission to test the new equipment. Halderman’s report, submitted to the court in July, describes “highly exploitable vulnerabilities that allow attackers to change votes despite the State’s purported defenses.” The judge immediately sealed the report “for attorney’s eyes only,” but Halderman petitioned for release of an abridged version that would increase transparency while restricting the sort of details that could benefit attackers. In October, the Department of Homeland Security’s cybersecurity group expressed interest in obtaining a copy of the report.
“Voters need to know their choices are recorded and counted in a process that is transparent and accurate. But officials can’t just dictate voter confidence. The system must earn their confidence,” said Marilyn Marks, executive director of Coalition of Good Governance.
So, how can voters be assured their votes actually get counted as cast?
It’s not like a bank account where you can verify your balance. Once in the system, votes are an anonymous collection no longer linked to any individual. “The best way to confirm outcomes is to count a sample of ballots manually and transparently, using robust audit protocols,” Marks said. “And the ballots must be hand-marked, not computer-marked. Unfortunately, all in-person voting in Georgia is on touchscreen ballot marking devices.”
Activists maintain that a ballot marking device is an overpriced alternative to hand-marking a paper ballot with a pen. A voter makes selections on the screen, the device prints the selections, and the voter casts the printout as the official ballot. Originally developed as assistive technology for voters who want help marking a ballot independently, ballot marking devices are now marketed for all voters, completely replacing hand-marked ballots at the polls. But the device can be hacked to print the wrong votes. The low-tech paper ballot, marked by the voter’s hand, is the one truly reliable ballot. Forcing BMDs on all in-person voters is not only technology overkill, it creates more unreliable ballots.
Ballot marking devices are replacing similar 2000s-era devices in Georgia, Pennsylvania, and many other jurisdictions nationwide. The older devices, direct recording electronics, or DREs, are what Smith caught dropping votes in Memphis and, in Georgia’s 2018 midterms, DREs apparently failed to record an estimated 127,000 votes for lieutenant governor. The Georgia race was featured in the documentary Kill Chain: the Cyber War on America’s Elections. Ultimately, in a landmark federal case brought by Marks’s group, the court declared the DRE system unconstitutional because it couldn’t be trusted to record or count votes correctly, and its results were not auditable.
This sounds familiar. In fact, evidence shows that newer doesn’t mean better. From the annual DEFCON hacking conference, to the many voting system experts studying them, BMDs are just as bad as their earlier cousins, or worse. In a heavily redacted court declaration in the case against Georgia’s ballot marking devices, Halderman wrote, “Plaintiffs cannot be assured that the personal votes each of them casts on BMDs as individual voters will be counted correctly or perhaps at all. … Georgia’s new BMD equipment is even easier to compromise than the DRE equipment it replaced.”
Halderman’s assessment is unsurprising since experts have already catalogued serious failings, notably the basic design flaw common to all BMD models, and additional flaws of some of the newest models. In a real-life example, the BMDs that are the subject of Free Speech for People’s lawsuit miscounted votes in a Northampton County election. “The error was noticed only because the vote totals were so obviously wrong,” Greenhalgh said.
But if a ballot marking device prints the wrong votes, wouldn’t voters notice?
“Many voters don’t even look at their printouts, or they just glance at them,” Marks said. Study after study confirms that voters don’t notice errors. The latest research found that only 40 percent of voters even look at their printouts, and just 6.6 percent report errors.
“The evidence is conclusive,” Greenhalgh said. “Voters don’t verify paper records produced by BMDs, so they should not be considered ‘voter-verified’ ballots.” Despite this conclusion, BMDs continue to be marketed with the notion that their printouts are equally reliable as hand-marked ballots in an audit. This has caused misperceptions to grow with even elections officials recommending “auditable paper ballots” like those used in Georgia in 2020 to “show the accuracy of the election results.”
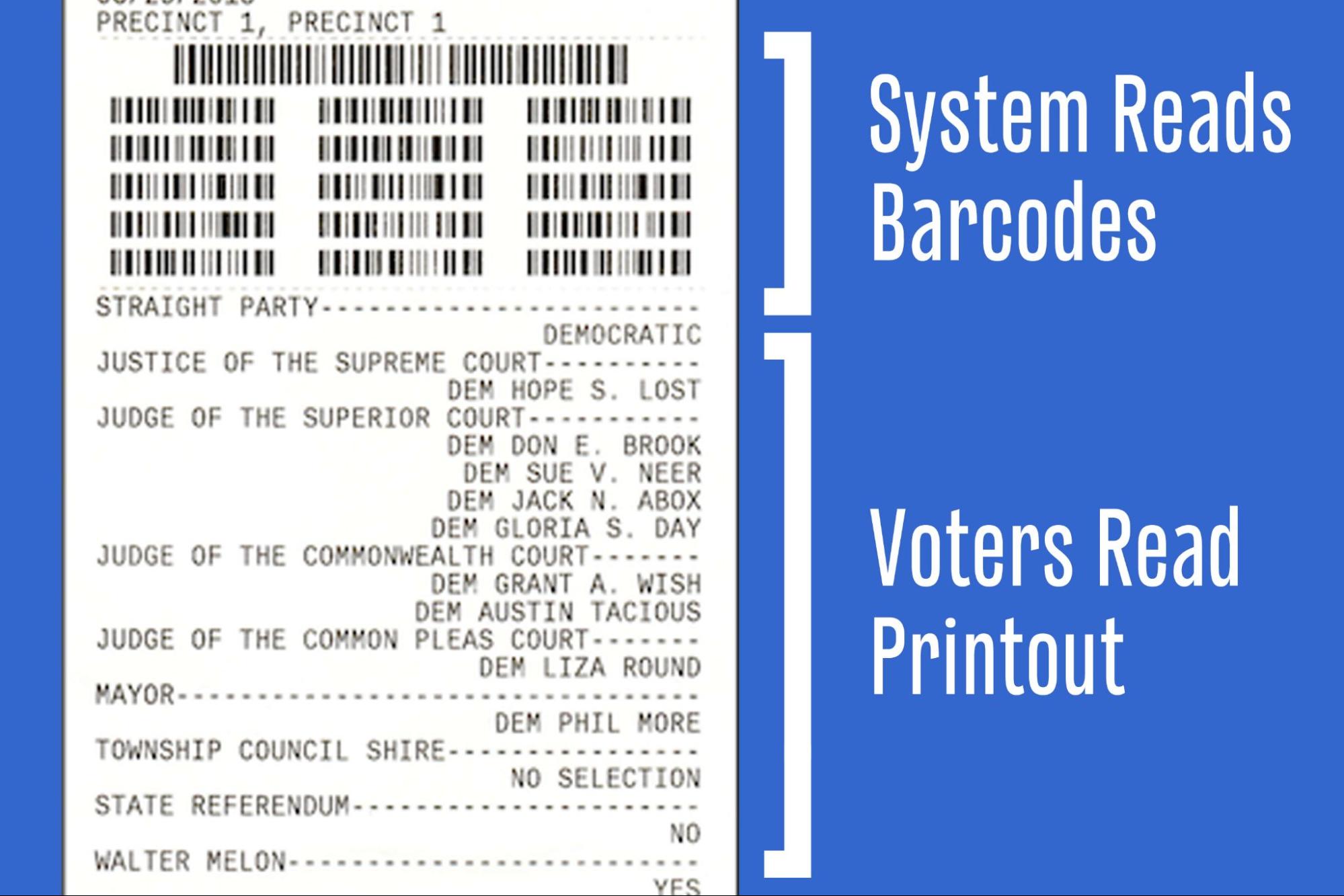
The devices have other problems. They’re expensive to purchase, store, and maintain. And they create long wait times at the polls.
“The answer is so simple,” Greenhalgh said. “Hand-marked ballots as the primary voting method with BMDs easily available to voters who want them. This is currently the most popular method of voting, and what computer scientists have long advocated. Then, to verify outcomes, elections must be followed by robust canvassing, ballot accounting, and auditing protocols for all contests.”
If the answer is simple, why is the problem so sticky? “Because it’s invisible,” Marks said. The process happens inside computers. “We must get realistic and face this threat. The ‘stop-the-steal’ advocates have a contorted view of election infrastructure and processes. And they’re determined to avenge Trump’s loss.” She and Greenhalgh fear mistrust and unrest will escalate into the 2022 midterms.
“Then there are deniers on the other extreme who say there’s nothing wrong with our voting systems,” Marks said. Meanwhile, election software was stolen in Colorado and distributed on the internet. Ransomware and supply chain attacks are occurring almost daily. “Our defenses are down, and the threat has escalated,” she said.
Marks, Greenhalgh, Smith, and many other voting and computer experts have eyes wide open about our election system, dedicated to making it more transparent and accountable. “We can no longer expect the public to trust what’s unworthy and invisible,” Marks said.



