Experts say barcode ballot marking devices lack transparency and security, and their vulnerabilities will attract insider threats of the kind Trump supporters have been charged with.
|
Listen To This Story
|
Election technology experts are warning that barcode ballot marking devices (BMDs) are vulnerable to bad actors capable of committing the perfect crime: changing the information on a ballot and getting away with it without the voter even realizing it happened.
The use of barcodes is one of these machines’ biggest downsides.
When people vote with these BMDs, they fill out their ballot on a screen; a printer then produces a paper ballot marked with a barcode. To cast their ballot, users feed this paper into a third device that scans the barcode to record the vote. And that’s a problem.
“Voters can’t read barcodes,” said Alex Halderman, professor of computer science and director of the Center for Computer Security and Society at the University of Michigan. “The problem is that you’re putting a potentially compromised computer in between the voter and the permanent and only record of their ballot.”
Their susceptibility to these types of attacks is not the only problem; BMDs are also difficult to adequately test and audit, according to a 2022 research report from the University of California, Berkeley.
The report demonstrates that even a small percentage of votes changed in a cybersecurity attack can alter the overall margin of results. It found that changing the votes on just 1 percent of ballots in a jurisdiction can alter the margin of a contest jurisdiction-wide by 2 percent, even if there are no undervotes or invalid votes.
“All of those concerns about someone manipulating the software — to change the election or to even just create chaos and distrust — apply equally, or even more, to people who have had insider access.” — Will Adler
“My right to vote also includes my right that all of my fellow citizens’ votes are not hacked,” said Andrew Appel, professor of computer science at Princeton University. “So it’s not just an individual, per-person choice. The security of our elections depends on everyone’s ballot not being hacked.”
And with elections just around the corner, awareness of security challenges is growing rapidly.
To date, virtually all attention that officials have paid to the security of the vote tabulation process has been directed at hackers, including foreign entities, penetrating the systems from outside.
But Will Adler, a senior technologist in election and democracy at the Center for Democracy and Technology, said he is also worried about an insider threat.
“All of those concerns about someone manipulating the software — to change the election or to even just create chaos and distrust — apply equally, or even more, to people who have had insider access,” he said.
And some election officials have already tried. In March of 2022, Mesa County Clerk Tina Peters was indicted on 10 counts of tampering with election equipment and misconduct, according to a district court record obtained by The Washington Post.
Peters is accused of sneaking an unauthorized person into a voting machine software installation — what election officials call a trusted build — and downloading sensitive hard-drive information from the voting machines in her county. And others have made similar attempts.
Earlier this week, a Reuters investigation showed that Matthew DePerno, a candidate to become Michigan’s next attorney general, gained unauthorized access to voting equipment. DePerno’s breach of security is one of four similar incidents at Richfield Township, according to court filings and public records first obtained by Reuters.
While Peters is being prosecuted, hackers of barcode BMDs may not be as easy to catch.
Experts say this is an issue without an easy fix. There are a number of factors that complicate the matter, one being that most voters do not routinely check their ballots: In one experiment where voters engaged with BMDs that were deliberately hacked to change their selections, only 6 percent of voters noticed that their vote was recorded incorrectly.
The voters were brought to a mock polling location to interact with touch-screen voting machines modified to operate as malicious BMDs. Each participant, unaware there would be any errors, voted on the touchscreen and printed the ballot. And on each of the ballots printed, the BMD had changed the selection of the participant.
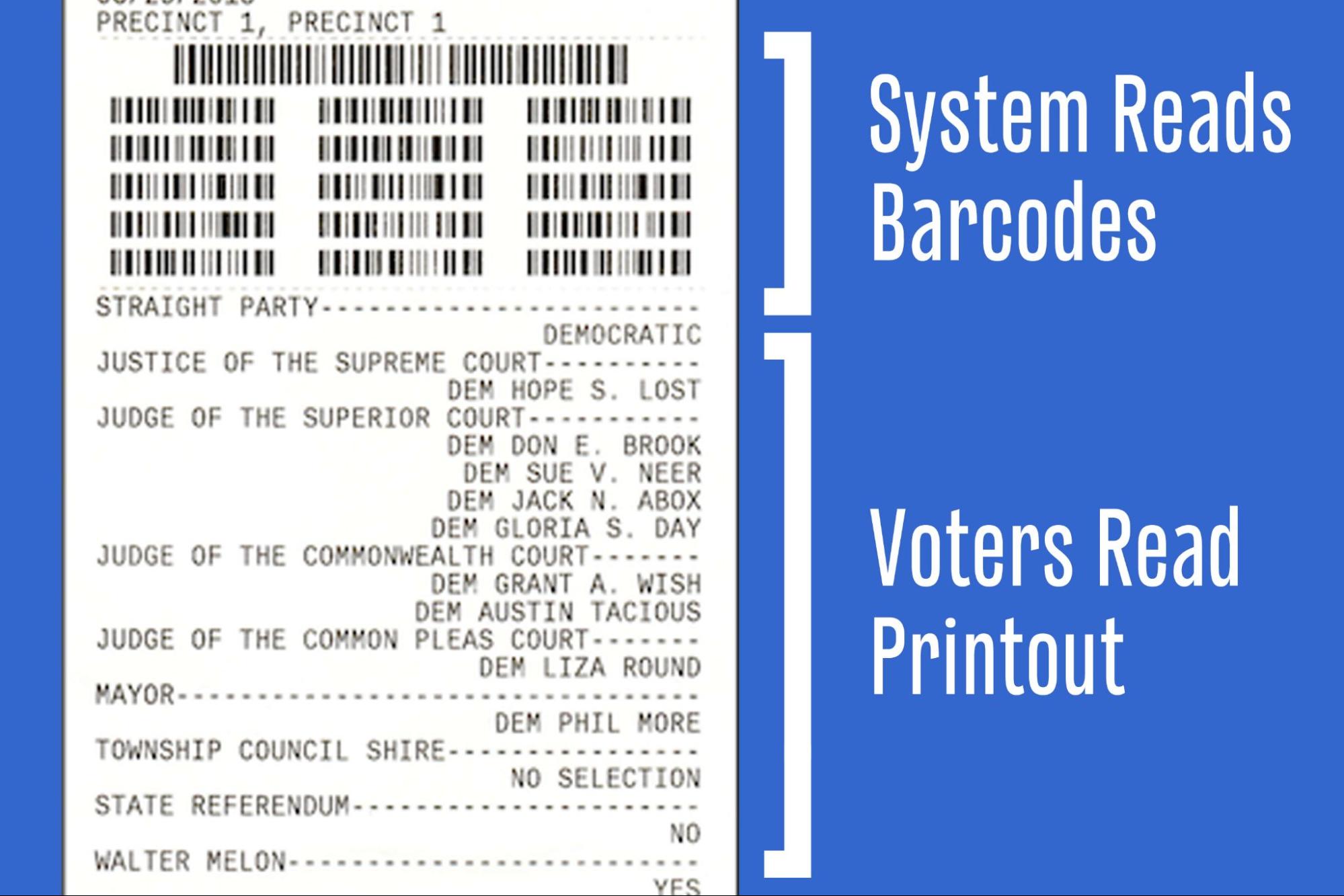
Halderman, who worked on the experiment, added that many voters who do notice something wrong with their ballots blame themselves.
“The notion that machines could do something wrong, it’s rather alien to people,” he said.
And other experts discovered similar findings. Philip Stark, professor of statistics at UC Berkeley, has conducted similar studies. He stressed that relying on voters to recognize a mistake on their ballots and inform a poll worker is not a dependable mode of troubleshooting because “there’s very little hope voters will notice errors.”
The Paper Trail
At a recent House Committee on Homeland Security hearing, lawmakers discussed improving cybersecurity measures to better protect the integrity of elections from outside attacks. The solution, experts said, is not that simple.
“Better cybersecurity cannot solve this problem anytime in the foreseeable future,” Appel said. “Our cybersecurity technology as of this decade is not strong enough to be able to guarantee the protection of these voting machines against some hacker who manages to install fraudulent software.”
The remedy is universal use of paper ballots, he added. And while other experts agree that a hand-marked paper ballot is the most secure way to vote, they said that a paper record per se is not necessarily sufficient.
“Paper itself is not a solution. It needs to be paper that you can trust, [that] reflects the voter’s selections,” Stark said. “And you’ve got to keep track of it and be able to demonstrate that you kept track of it.”
Stark believes that, looking to upcoming elections, more rigorous audits will greatly help to mitigate election security concerns. Human beings, equipment, and software are fallible, he added, and routine audits are a way to correct and monitor those concerns.
“In an election without rigorous audits, barcode attacks might change the result of that election.” — Alex Halderman
“I would love to see jurisdictions move to a much more serious concern for the scrutiny of the trustworthiness of the paper trail,” he argued. “And then routinely auditing the outcome of every contest to make sure that nothing went wrong that altered the result.”
Halderman said audits are even more important in close elections.
“There’s a rigorous mathematical way of deciding how much you have to audit to be confident in some well-defined sense that the outcome wasn’t changed by computer error or fraud,” he argued.
A rigorous audit would be ideal for every election, he added. But in practice, most states do not conduct these types of audits. Halderman explained that there are a variety of reasons for this. Some states, he said, still do not have a paper trail of every vote. In other states, where there is a paper record, state-level officials don’t have the legal authority to require counties to participate in a rigorous audit. There’s also a learning curve to understanding risk-limiting audits that he said some election officials have not overcome yet.
“In an election without rigorous audits, barcode attacks might change the result,” he emphasized.
At a time in which mistrust in elections has been stoked, the opaqueness of BMDs poses a problem even if the vote counting goes entirely by the book. Halderman noted that accusations of fraud can spread much more easily if election processes are not transparent. And barcode BMDs are a prime example.
“People who want to delegitimize the results of elections will go to the ballot marking devices and risks and point out that we don’t have a good way to know whether we had a malfunction or not,” he concluded.
This story was written by a member of our Mentor Apprentice Program (MAP). It gives aspiring journalists an opportunity to hone their craft while covering national and international news under the tutelage of seasoned reporters and editors. You can learn more about the MAP and how you can support our efforts to safeguard the future of journalism here.