Kemp’s Aggressive Gambit to Distract From Election Security Crisis
Georgia Announces Hacking Investigation Into Democrats, but What Really Happened?
Georgia Secretary of State Brian Kemp, battling in a close race to become governor, is pushing back against new reports of election vulnerabilities — uncovered by WhoWhatWhy — distracting the media and voters. He’s charging those who reported the danger with… being the danger.
When Georgia Democrats were alerted to what they believe to be major vulnerabilities in the state’s voter registration system Saturday, they contacted computer security experts who verified the problems. They then notified Secretary of State Brian Kemp’s lawyers and national intelligence officials in the hope of getting the problems fixed.
Instead of addressing the security issues, Kemp’s office put out a statement Sunday saying he had opened an investigation that targets the Democrats for hacking.
Kemp’s statement has become top news nationwide, but the context and background have yet to be reported — so we are providing it below.
The Backstory and Detail
.
By the time Democrats reached out to the experts, Kemp’s office and the Federal Bureau of Investigation had already been alerted to the problem on Saturday morning by David Cross of the Morrison Foerster law firm. Cross is an attorney for one of the plaintiffs in a lawsuit against Kemp and other elections officials concerning cyber weaknesses in Georgia’s election system.
A man who claims to be a Georgia resident said he stumbled upon files in his My Voter Page on the secretary of state’s website. He realized the files were accessible. That man then reached out to one of Cross’s clients, who then put the source and Cross in touch on Friday.
The next morning, Cross called John Salter, a lawyer who represents Kemp and the secretary of state’s office. Cross also notified the FBI.
WhoWhatWhy, which exclusively reported on these vulnerabilities Sunday morning, had consulted with five computer security experts on Saturday to verify the seriousness of the situation. They confirmed that these security gaps would allow even a low-skilled hacker to compromise Georgia’s voter registration system and, in turn, the election itself. It is not known how long these vulnerabilities have existed or whether they have been exploited.
Just before noon on Saturday, a third party provided WhoWhatWhy with an email and document sent from the Democratic Party of Georgia to election security experts that highlighted these potential vulnerabilities within the state’s My Voter Page and online voter registration system.
According to the document, it would not be difficult for almost anyone with minimal computer expertise to access millions of voters’ private information and potentially make changes to their registrations — including canceling them.
In this election and during the primaries, voters have reported not showing up in the poll books, being assigned to the wrong precinct, and being issued the wrong ballot.
All of that could be explained by a bad actor changing voter registration data.
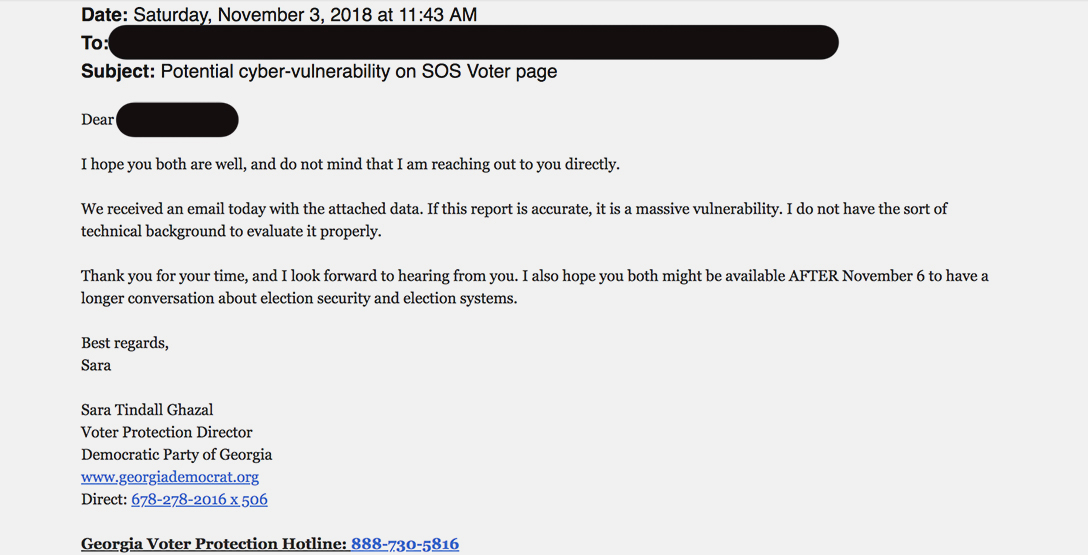
In the email that sparked this controversy, Sara Tindall Ghazal, the voter protection director for the Democratic Party of Georgia, alerted two computer experts of a potential problem that she said might constitute a “massive vulnerability.” WhoWhatWhy is not publishing the document describing the problem, as it provides a roadmap to exploiting the security weaknesses.
None of the cyber security experts WhoWhatWhy then contacted tested the vulnerabilities described, downloaded any files, altered any data, or searched the My Voter Page by altering the website address.
All five noted that testing these vulnerabilities without permission would be illegal.
Instead, several logged onto the My Voter Page to look at the code used to build the site — something any Georgian voter could do with a little instruction — and confirmed the voter registration system’s vulnerabilities.
They then alerted a national intelligence agency and reached out to the Coalition for Good Governance, an election security advocacy group that has sued Georgia multiple times over the vulnerability of its systems.
Bruce Brown, a lawyer for the group, then reached out to Kemp’s attorneys to alert them of the problem. At 7:03 PM Saturday night, he emailed John Salter and Roy Barnes, former governor of Georgia, in their capacities as counsel to Secretary of State Kemp, to notify them of the serious potential cyber vulnerability in the registration files that had been discovered without any hacking at all, and that national intelligence officials had already been notified.
WhoWhatWhy published its first story on the subject shortly after 6:00 AM Sunday morning.
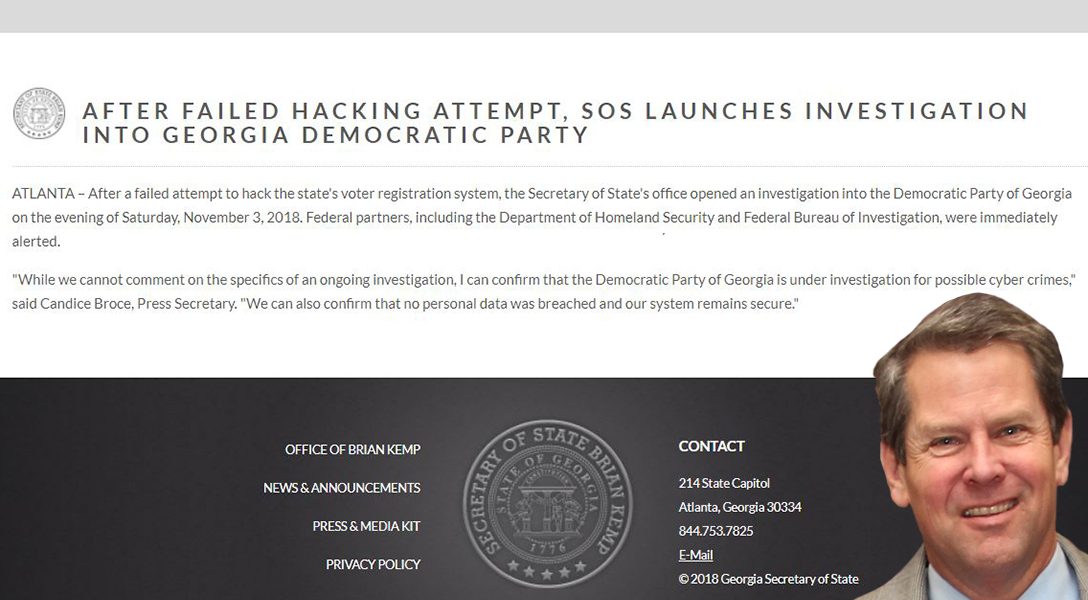
Instead of addressing the problem, however, Kemp put out the statement an hour later saying his office has launched a hacking investigation.
“While we cannot comment on the specifics of an ongoing investigation, I can confirm that the Democratic Party of Georgia is under investigation for possible cyber crimes,” press secretary Candice Broce stated. “We can also confirm that no personal data was breached and our system remains secure.”
Kemp’s office is being disingenuous, Brown asserted.
“We have seen, unfortunately, that we were too correct in our allegations and Judge [Amy] Totenberg was too prescient in her concerns about the system,” Brown said. “That Kemp would turn this around and blame other people for his failures is reflective of his complete failure as Secretary of State.”
Judge Totenberg had recently ruled that there was not enough time for Georgia to switch to paper ballots — widely seen as a more secure voting method — but expressed grave concerns over the security of the state’s elections.
“What is particularly outrageous about this, is that I gave this information in confidence to Kemp’s lawyers so that something could be done about it without exposing the vulnerability to the public,” Brown told WhoWhatWhy. “Putting his own political agenda over the security of the election, Kemp is ignoring his responsibility to the people of Georgia.”
It is not clear what impact — if any — the vulnerabilities identified will have on Tuesday’s elections, or how they might have affected early voting. Voters should still go to the polls and, if they are encountering problems, ask to cast a provisional ballot as is their right.
The computer security experts with whom WhoWhatWhy spoke were all baffled by what they found when they reviewed the problem.

“For such an easy and low hanging vulnerability to exist, it gives me zero confidence in the capabilities of the system administrator, software developer, and the data custodian,” Kris Constable, who runs a privacy law and data security consulting firm, told WhoWhatWhy. “They should not be trusted with personally identifiable information again. They have shown incompetence in proper privacy-protecting data custodian capabilities.”
As Secretary of State, Kemp is the data custodian, meaning he is responsible for the security of voter information. The system administrator works for Kemp and the software developer is a private contractor hired by Kemp’s office.
Kemp is also the Republican candidate for governor in Tuesday’s election, where he is locked in a close race with Democrat Stacey Abrams.
The first vulnerability identified in the email is on the My Voter Page, where voters can check their registration, the status of their mail-in or provisional ballots, or change their voter information. After following a commonly used link, one arrives at a page that is not secure. To view any file on the server that runs the My Voter Page nothing more is needed than typing any file name into the web browser, the experts said.
In addition to documents, files include things like network configuration files, cryptographic keys, and possibly even code that could be used to break into the server.
Because it would be illegal to explore what is available on the site, the extent of the vulnerability is still not known.
“Holy shit,” Duncan Buell told WhoWhatWhy when he logged onto the website. “Presumably, you could just hit the backspace button on the file, put in a new file name, and it would let you download that.”
Even if someone didn’t know the name of the document they were trying to access, they could instead find it by writing a code to probe the My Voter Page, said Buell, a computer science professor at the University of South Carolina and elections and voting technology expert.
The second vulnerability described in the email is found in the state’s online voter registration system.
In the code of the website — which anybody can access using their internet browser — there is a series of numbers that represent voters in a county. By changing a number in the web browser’s interface and then changing the county, it appears that anybody could download every single Georgia voter’s personally identifiable information and possibly modify voter data en masse.
In addition, voter history, absentee voting, and early voting data are all public record on the secretary of state’s website. If a bad actor wanted to target a certain voting group, all of the information needed is available for download.
“It’s so juvenile from an information security perspective that it’s crazy this is part of a live system,” Constable said.
What’s more, there don’t seem to be any security measures that could detect these changes or trace them back to a source, according to several of the experts.
Worse yet, a bad actor could easily pretend to be someone else, according to Constable. “In theory you could copy and paste that session ID or cookie — that unique string — and put it in your browser to emulate that person,” Constable said. “So not only could you access that person’s information and act as that person, you could then make changes under that person’s identity.”
Changes to voter registration information could create chaos on Election Day: long lines to vote, voters going to the wrong precinct, voters being given the wrong ballot, or not showing up on the polls at all.
Georgia may not be alone. These security flaws may well exist in other states.
A Connecticut-based private contractor, PCC Technologies Inc., has contracts to manage voter registration systems for Georgia and 14 other states. PCC also runs online voter registration for six of them, including Georgia. If these vulnerabilities exist in Georgia, they could also be present in other states where PCC operates.
Matt Bernhard, a Ph.D. student in computer science at the University of Michigan focusing on voting technology, found that personally identifiable information could also be accessed through North Carolina’s voter page, which PCC also manages.
As Georgia’s system has not been audited — if it had, these problems would have been found and fixed, presumably — there are likely other vulnerabilities that could impact the midterm election, according to Constable.
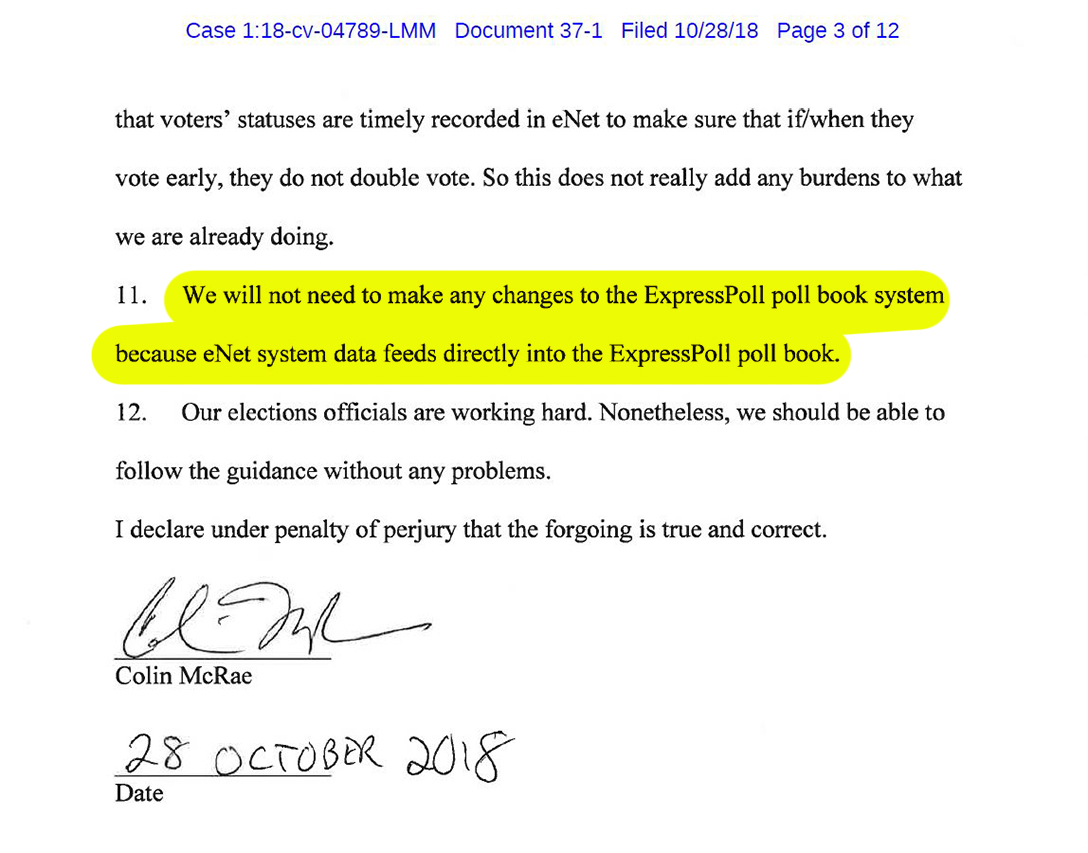
PCC also runs the ElectioNet system, which is used by every county in Georgia to manage the state’s voter rolls. If voter registration data was changed, it would show up in the ElectioNet system. In a declaration as part of a recent lawsuit against the state, Colin McRae, chair of the Chatham County Board of Registrars, disclosed that the ElectioNet system is also responsible for populating the data in the pollbooks of every state.
The pollbooks are used to encode the voters’ yellow access cards on Election Day. Those cards have voters’ ballot style numbers, which are then brought up by the voting machine. The connection between ElectioNet and the pollbooks draws a straight line between how security gaps on the My Voter Page and voter registration site could impact the election, including giving voters the wrong ballots or removing them from the rolls.
If the assessment of these vulnerabilities is accurate, it would be the fourth time in as many years that the private information of every voter in Georgia, as well as other information related to voting, has been exposed.
In 2015, an employee at the secretary of state’s office sent out personally identifiable information to 12 news media and political party organizations.
At the time, Kemp said that “all 12 discs have been recovered or confirmed they were destroyed by the recipients. I am confident that all voter information is secure and safe.”
The press release also said that Kemp was “in the process of engaging Ernst & Young, a top professional services firm with specialization in IT security, to conduct a thorough, top to bottom review of our IT policies and procedures.”
In August, 2016, computer researcher Logan Lamb, formerly of Oak Ridge National Laboratory, was able to access Georgia’s entire voter registration database, including all personally identifiable information. The system was not password protected and was vulnerable to being rewritten. He notified the state of the problem.
Then in February, 2017, Christopher Grayson — a Los Angeles-based security engineer — and Lamb found that the problem had not been fixed and that the same information was still unprotected.
The Coalition for Good Governance sued Kemp in July of 2017 in an attempt to replace the electronic voting system with paper ballots and to secure the electronic poll books, citing the previous security breaches.
Kemp is also the Republican candidate for governor, running against Democrat Stacey Abrams. Kemp has ignored calls to step down as secretary of state — most recently by former President Jimmy Carter — opting instead to both run the election and be a participant.
In a statement made to NPR’s Atlanta affiliate WABE in July of this year, a spokesperson for the secretary of state said, “There has never been a breach in the Secretary of State’s office. We have never been hacked, and according to President Trump and the Department Of Homeland Security, we have never been targeted. Georgia has secure, accessible, and fair elections because Kemp has leveraged private sector solutions for robust cyber security, well before any of those options were offered by the federal government.”
According to three experts who reviewed the security features of the My Voter Page and voter registration website — not just its vulnerabilities — Kemp would have no way of knowing if the site had ever been hacked or by whom. PCC, the private-sector company responsible for managing Georgia’s voter registration and online voter registration systems, seems to be at fault for the poorly designed site.
“Not only could anybody in the world access it, but there’s not even any indication that there are protections built in to detect an intrusion, otherwise this would have been discovered and corrected already,” Constable said.
Harri Hursti, a world-renowned data security expert who has studied election cybersecurity in five countries, including the US, is familiar with a different weakness in Georgia’s voting infrastructure. In a series of tests that became known as the “Hursti Hacks,” the researcher hacked the Diebold voting system — the same type of voting machines used in Georgia.
But even he was stunned by the vulnerabilities in Georgia’s My Voter Page and voter registration system.
“This is the equivalent of having the bank safe door open,” Hursti said. “And while it’s open, you have the bank safe code posted on the door. People who have built this have no idea what they’re doing.”