Brian Kemp and His Staff Caught in a String of Falsehoods
Election System Security Worse Than Previously Understood
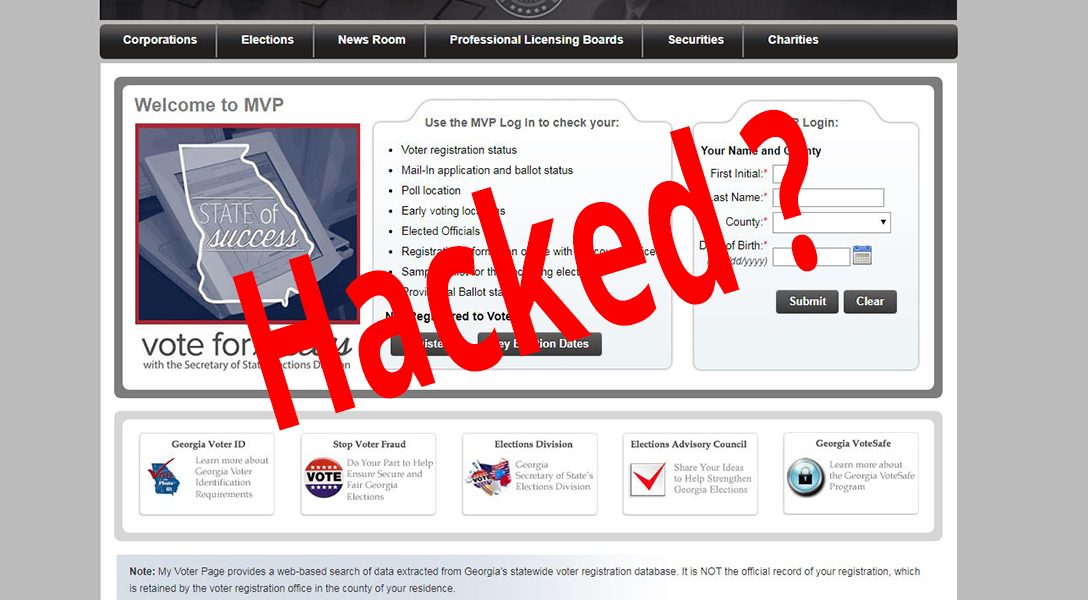
In response to WhoWhatWhy’s exclusive story on vulnerabilities in Georgia’s voter registration system, Secretary of State Brian Kemp’s office has made unsubstantiated claims and omitted inconvenient truths about the security of that system. Here is new information on the risks.
Since WhoWhatWhy exclusively revealed major security gaps in Georgia’s voter registration and voter information websites — vulnerabilities severe enough to potentially compromise the election — the secretary of state’s office has made a series of statements that are unfounded and, frequently, outright false.
Brian Kemp is the Republican candidate for governor in Tuesday’s election against Democrat Stacey Abrams. But he is also Georgia’s secretary of state, putting him in charge of the state’s elections mechanism while also competing in the marquee contest.
The first statement from the secretary of state’s office in response to the vulnerabilities identified in WhoWhatWhy’s reporting, alleged, without evidence, that the Democratic Party of Georgia had attempted to hack the state’s voter registration system.
By that time, WhoWhatWhy had already reported the actual story: the system’s vulnerabilities were brought to the attention of Georgia’s Democrats, who then asked computer experts to verify the security gaps. Once the problems were confirmed, Kemp’s lawyers and national security officials were notified on the same day.
Kemp’s office mentioned none of these facts in its initial statement.
Computer security experts were concerned that the web vulnerabilities could have implications for elections across the country.
Instead, it quoted press secretary Candice Broce, who said that “[the secretary of state] can also confirm that no personal data was breached and our system remains secure.”
However, this assurance came without evidence and contradicted expert opinions. According to the computer security experts WhoWhatWhy consulted in its reporting, the voter websites did not seem to have any mechanism to track a data breach. The secretary of state’s office has not clarified how they were able to confirm that no personal data was breached.
In addition, we have now learned much more about the risks involved, and share those with our readers below.
When the State Found Out
.
In accusing the Democratic Party of Georgia of wrongdoing, Kemp’s office failed to mention that it had already been notified of the very same vulnerabilities 24 hours earlier.
A lawyer suing Kemp over the state’s insecure election system, David Cross, notified the Secretary of State’s office of the vulnerabilities on Saturday morning, he told WhoWhatWhy. He also notified the FBI. Hours later, Richard Wright, the Georgia citizen who first noticed the security problems on his own My Voter Page, shared the information with the Democratic Party through an intermediary, according to email exchanges between Cross and the Georgia voter. (WhoWhatWhy did not identify Wright in its original reporting because he had asked Cross not to share his name. Other national news outlets identified Wright following WhoWhatWhy’s breaking story.)
In a statement to ProPublica regarding the investigation into the Democrats, Broce said, “All you need, to open an investigation, is information suggesting plans and an attempt to put together some kind of program or utilize specialize tools to find a vulnerability.”
The secretary of state’s office had the information showing the vulnerabilities before the Democrats did. This provides the public with a clear example of how Kemp uses his discretion as secretary of state to support his own gubernatorial campaign, in what would appear to be a glaring conflict of interest.
The office also knew that the information came from a private citizen, not from the Democratic Party of Georgia.
When the Democrats received the information, it was passed to Sara Ghazal, who leads their voter protection efforts. Ghazal reached out to computer security experts who confirmed the vulnerabilities, then contacted federal officials.
Despite Broce’s claim that no vulnerability existed and no action was needed, changes were made to improve the security of the state’s My Voter Page and voter registration page throughout the day.
Since Georgia’s voter registration is run by the private contractor PCC Technologies Inc., which also contracts with 14 other states for the same service, the computer security experts were concerned that the web vulnerabilities could have implications for elections across the country.
And since anyone in the world connected to the internet could access the site, the experts contacted federal officials dealing with the national security implications of cyber attacks (WhoWhatWhy’s source would not confirm which agency the experts contacted, only that they were not law enforcement).
By Saturday afternoon, Matt Bernhard, a computer security expert and Ph.D. student in computer science at the University of Michigan, confirmed that North Carolina, another client of PCC, had the same vulnerability in its voter registration system.
On Saturday evening, Bruce Brown, another lawyer in a lawsuit against Kemp over mail-ballot rejections, also notified the secretary of state’s office of the vulnerabilities.
By the time the secretary of state’s office announced its investigation into the Democratic Party of Georgia, it had been notified twice of the vulnerabilities, national security officials had been notified, and the FBI had been notified, all by lawyers already suing Kemp or by computer security experts contacted by the Democrats.
Yet none of this has ever been mentioned by Kemp or anybody else in the secretary of state’s office.
As of 12:00 AM on Monday, the vulnerabilities had not been addressed, according to one computer security expert.
How The State Responded
.
WhoWhatWhy asked the secretary of state’s office if it planned to conduct an audit to ascertain that unauthorized changes had not been made to voter registrations.
Broce responded, “There is no such vulnerability in the system as alleged by your article. We immediately reviewed those claims and could not substantiate any of it. To be clear, those webpages are not linked to a location containing files with confidential or sensitive information.”
The five computer security experts WhoWhatWhy contacted disagree. Each expert — Matt Bernhard, Duncan Buell, Kris Constable, Harri Hursti, and one source who asked to remain unnamed — is a national or international leader in cyber or elections security.
“This is ‘101 Broken. This is the most trivial thing you can do wrong. If you have any sense of security, this is not what you do. This is a high school project.”
And despite Broce’s claim that no vulnerability existed and no action was needed, changes were made to improve the security of the state’s My Voter Page and voter registration page throughout the day.
WhoWhatWhy was on the phone with an additional expert — who asked to remain unnamed due to concerns about the secretary of state’s investigation tactics — as he watched the My Voter Page get updated while logged into his own voter account.
“They’re updating the page on the night before the election,” he said. “This is wild.”
WhoWhatWhy asked Broce why the page was being updated if it was secure, as she had previously claimed.
“It is standard practice to prepare the My Voter Page for high volume on Election Day,” Broce wrote in an email. “This configuration accounts for anticipated traffic with hundreds of thousands of individuals using the system.”
She provided a slightly different answer to ProPublica, saying, “we always move our My Voter Page to a static page before Election Day.” ProPublica noted that did not seem to be accurate.
In addition to the vulnerabilities WhoWhatWhy’s reporting revealed on Sunday, two more were found. Both seem to have been fixed during Monday’s updates.
The first was on the homepage of the state’s My Voter Page. The “cross-site scripting vulnerability” could have enabled bad actors to control the web browser of anyone trying to access the page. That would allow them to steal passwords, direct the target’s browser to a malicious website, and download computer viruses. If that happens, a bad actor could gain complete control of that computer.
The second vulnerability was in the connection between the My Voter Page server and the ElectioNet server, a service run by PCC for managing the state’s voter registrations. A single web script was running across both servers, leaving them open to what’s called a “man-in-the-middle” attack.
“This is ‘101 Broken,” cybersecurity expert Harri Hursti said. “This is the most trivial thing you can do wrong. If you have any sense of security, this is not what you do. This is a high school project.” Hurst has studied cybersecurity and elections systems in five countries, including the US.

However, Broce claims that the secretary of state’s office contracts with “top-notch cybersecurity vendors for firewall protection, around-the-clock monitoring of network traffic, and related security protections to watch for this information.”
Broce declined to name those vendors, citing an exemption in Georgia’s open-record laws. When WhoWhatWhy asked Broce to point to the specific part of the law that allowed her to claim exemption, she declined to respond.
On October 1, WhoWhatWhy had asked Broce if the secretary of state or any Georgia office outsourced management of the voters’ database to a contractor in another state.
On October 4, Broce replied, “The answer is no.”
Yet WhoWhatWhy’s reporting revealed that the secretary of state has been using PCC’s ElectioNet Election Management software since 2012, according to a press release on PCC’s website. PCC is based in Connecticut.
The secretary of state contracts with PCC. The company provides the state with trademarked “Election Management” software and is based in Connecticut. When asked why Broce previously told WhoWhatWhy that management of the voter’s database was not outsourced to an out-of-state vendor, Broce wrote in an email that there are “in-house staff who manage this system.”
This indicates that the secretary of state only purchases the software from PCC and has its own staff who are in charge of the day-to-day operations.
Broce declined to identify the staff in reference and directed WhoWhatWhy to file an Open Records Request, which we have done. It is not clear who is responsible for fixing flaws in system security — or for designing such a poorly protected system in the first place.
Kemp’s Office Has Been Here Before
.
The sequence of events from the last 72 hours — data from the state’s election system is exposed online, national and international cybersecurity experts confirm the seriousness of the matter, and the state attempts to deflect those concerns — have been seen before.
In a September 17 ruling in which she declined to order that Georgia use more secure paper ballots in the midterm elections, accepting the state’s argument that this was impossible due to time constraints, Judge Amy Totenberg nonetheless addressed this pattern head on: “Advanced persistent threats in this data-driven world and ordinary hacking are unfortunately here to stay. [The State] will fail to address that reality if they demean as paranoia the research-based findings of national cybersecurity engineers and experts in the field of elections.”
“The Court is gravely concerned about the State’s Case pace in responding to the serious vulnerabilities of its voting system,” Totenberg continued. “[F]urther delay is not tolerable in their confronting and tackling the challenges before the State’s election balloting system.”
Nonetheless, in the September 12 hearing on the same case, it also became clear that Kemp’s office has not moved to hire staff with sufficient cybersecurity expertise. Answering questions under oath, Michael Barnes, director of the state’s Center for Elections Systems, admitted, “I’m not a computer scientist. And I don’t claim to be. And I have never written malicious code … I don’t write code.”
In the same hearing, Barnes was asked, “Has the Secretary employed a cyber security expert…?” Barnes replied, “I know that the CIO for the Secretary of State’s office has been highly engaged in analyzing how our systems are set up now within the Secretary of State’s office.”
Barnes’s answer refers to a CIO, or Chief Information Officer. He names as the CIO Merritt Beaver, whose LinkedIn page identifies 22 skills, none of which are cybersecurity. According to that page, Beaver is “an innovative technology executive … [and] a driven leader who is able to develop business strategy, implement change, [and] formulate and execute business plans to maximize corporate resources.”
To date, the secretary of state’s office — led by Kemp — has not identified a single computer expert or cybersecurity expert on staff, nor has it identified contractors who could provide those services.
That may explain why the online security lapses that WhoWhatWhy’s reporting detailed were so basic.
“The underlying thing here is that there are so many things wrong, that the whole system is vulnerable from just a URL manipulation,” Hursti said. “The whole thing is broken by design.”
As of this morning, on Election Day, at least that URL vulnerability has been fixed. But the data in the poll books? Voters have no guarantee that it’s accurate.
Timeline
.
Here’s the timeline of events to date:
Thursday, October 25:
- The Georgia citizen and registered voter, Richard Wright, who discovered the vulnerability, reaches out via Twitter to a plaintiff in a lawsuit against Kemp seeking improvement in election security.
.
Friday, November 2:
- 3:00 PM — Wright speaks with lawyer for three of the plaintiffs in the election security case, Curling v. Kemp. That lawyer is David Cross, from the Washington, DC, offices of the Morrison Foerster law firm.
.
Saturday:
- Early morning — Cross calls John Salter, a lawyer who represents Kemp and the secretary of state’s office, to notify him of the vulnerabilities, according to Cross.
- Early morning — Cross calls the Federal Bureau of Investigation to notify them of the vulnerabilities, according to Cross.
- Late morning — Wright notifies the Democratic Party of Georgia of the vulnerabilities, going through an intermediary, according to email records between Cross and Wright.
- 11:54 AM — The Democratic Party of Georgia reaches out to computer security experts to confirm the vulnerabilities.
- 12:57 PM — Computer experts confirm the vulnerabilities.
- One expert then notifies a non-law enforcement, federal office responsible for the national security implications of cyber attacks. Since Georgia contracts with the private company PCC Technologies Inc. to manage voter registration, and PCC contracts with 14 other states providing the same service, the vulnerabilities have national importance.
- 1:44 PM — Matt Bernhard, a computer security expert and Ph.D. student in computer science at the University of Michigan, confirms that North Carolina, another client of PCC, has the same vulnerability in its voter registration system.
- 7:04 PM — Bruce Brown, a lawyer for the Coalition for Good Governance, an election security advocacy group that has sued Georgia multiple times over the vulnerability of its systems, emails John Salter and Roy Barnes, former governor of Georgia, in their capacities as counsel to Secretary of State Kemp.
.
Sunday morning:
- 4:47 AM — WhoWhatWhy notifies Candice Broce, press secretary for the secretary of state’s office, that a story on the vulnerabilities will be published shortly. WhoWhatWhy requests comment on guarantees for securing the election.
- 6:00 AM — WhoWhatWhy posts its story on the vulnerabilities.
- 7:00 AM — The Secretary of State’s office posts a statement on its website alleging, without evidence, that the Democratic Party of Georgia attempted and failed to hack the state’s voter registration system, and that the Department of Homeland Security and the Federal Bureau of Investigations had been notified.
- 9:00 AM — WhoWhatWhy begins posting updates on the story, including evidence to show that the secretary of state’s allegations omit essential details of what has occurred.
.
Monday:
- 12:00 AM — Computer security expert confirms that all of the vulnerabilities are still active.
- 3:57 PM — ProPublica confirms that security updates are being made to the My Voter Page site
- 9:15 PM — WhoWhatWhy calls a computer security expert, who logs into his own account and watches live updates being made to the My Voter Page.
.
Tuesday:
- Election Day. Polls open.
.
Correction notice, 11/6/2018, 10:36 AM: An earlier version of this story incorrectly attributed the initial sharing of information regarding the vulnerabilities of the state’s election website to the Democratic Party as David Cross. The person was Richard Wright. Also in the timeline we clarified that Richard Wright reached out via Twitter to the plaintiff on October 25. We regret the error.