Alleged “hacktivist” Barrett Brown, the 31-year old mislabeled “spokesman” for the shadowy hacker collective known as Anonymous, faces federal charges that could put him away for over a hundred years. Did he engage in a spree of murders? Run a child-sex ring? Not quite. His crime: making leaked emails accessible to the public—documents that shine a light on the shadowy world of intelligence contracting in the post-9/11 era.
 [1]A critically acclaimed author and provocative journalist, Brown cannot be too easily dismissed as some unruly malcontent typing away in the back of a gritty espresso lounge. He is eccentric. And he was clearly high on something, if only his own hubris, when he made a threatening video that put him in the feds’ crosshairs. But that’s not the real reason for the government’s overreaction. Evidence indicates it has a lot more to do with sending a message to the community he comes from, which the government sees, correctly, as a threat.
[1]A critically acclaimed author and provocative journalist, Brown cannot be too easily dismissed as some unruly malcontent typing away in the back of a gritty espresso lounge. He is eccentric. And he was clearly high on something, if only his own hubris, when he made a threatening video that put him in the feds’ crosshairs. But that’s not the real reason for the government’s overreaction. Evidence indicates it has a lot more to do with sending a message to the community he comes from, which the government sees, correctly, as a threat.
The Barrett Brown case is simply the latest in a string of prosecutions in which the government pursues anyone involved in making information “liberated” from governmental or corporate entities easily accessible to the public. Those targeted are not necessarily accused of the illegal entry itself (the “hack”) or violating contracts (as in the case of a “leak”). These are people performing a function analogous to that of a newspaper—yet they can face prison sentences longer than those prescribed for murderers, rapists, and terrorists.
The Obama administration’s assault on accountability is dual-pronged: attack the messenger (as in the case of Brown, WikiLeaks, even New York Times reporters [3]) and attack the source (Bradley Manning [4], John Kiriakou [5], Thomas Drake [6], etc.). In fact, seven of those sources have been indicted as traitors under the 1917 Espionage Act during the Obama years alone—more than double the “espionage” charges against whistleblowers by all previous presidential administrations combined.
The Espionage Act is a draconian relic from World War I designed to prevent infiltration by foreign agents, like those of the Kaiser’s Germany. It has a sordid history as an instrument against American dissenters who leak to the media, including Pentagon Papers whistleblower Daniel Ellsberg, but has been used sparingly hitherto—until Barack Obama’s administration.

The government’s position is that revealing this information to the media enables “enemies” to see it. Thus, whoever blows the whistle is “aiding the enemy.” But in these cases, the enemy is the American people.
***
Brown, in federal custody since September 2012, has been jousting with the feds for quite some time.
Round one of his travails began on March 6, 2012, when FBI agents raided his Dallas apartment, looking for evidence related to the 2011 hack [7] of emails belonging to Stratfor—a private firm with substantial links to the American intelligence community. Brown sought refuge at his mother’s, but special agents arrived there as well, later in the evening. Although the feds found no incriminating evidence, they continued to harass Brown and his family, threatening to file obstruction of justice charges against Brown’s mother for hosting her son during the raid. This prompted Brown to record an ominous YouTube video threatening the special agent in charge of the investigation. He was arrested that evening and held for weeks without indictment, under the claim he was an imminent threat to the agent’s safety. In early October 2012, he was finally charged on a number of counts related to harassment of a federal officer.
In December of that year, while still in custody, he was indicted on an additional charge: “trafficking” in stolen material. Had he been shipping purloined goods across state lines? Hardly. His “trafficking,” according to the government, consisted of posting a link in a chat room.
On January 23 of this year came the coup de grâce. Brown was hit with a third round of federal charges [9]—this time for allegedly concealing evidence during that initial March 2012 raid on his apartment
Officially unrelated to these charges is the real nut of the government’s dispute with Brown: his personal initiative known as ProjectPM [10].
Barrett’s Baby
ProjectPM is a crowd-sourced research effort with several aims. First, to study 75,000+ emails pilfered by Anonymous from military and intelligence contractor HBGary Federal, and its parent company HBGary. Second, to post these raw, primary-source documents to a website where readers can edit and contribute further information. Third, to use these documents to map out the relationships between private contractors and the federal government that form our current national security state.
Brown’s work is a potential bonanza for journalists, as one of the few efforts to come to grips with the explosive growth of the private intelligence industry in the last decade.
From February 2011 until Barrett’s arrest in September 2012, ProjectPM had publicly identified the following revelations within the hacked emails:
– A conspiracy by lobbying and cybersecurity firms to engage in a disinformation and sabotage campaign against critics of the Chamber of Commerce and Bank of America.
– An operational mass surveillance and data-mining program targeting the Arab world.
– An unnamed project to utilize online “Persona Management with the intent of manipulating information or perception, conducting data mining, [and] infiltrating social organizations.”
– The employment of American PR firms to discredit and sabotage dissidents from Yemen, Saudi Arabia, and Bahrain.
***
It isn’t hard to see the parallel with the case of free-information activist Aaron Swartz. On January 17, WhoWhatWhy wrote about the U.S. attorney for Massachusetts, Carmen Ortiz, whose avid prosecution of Swartz preceded his suicide, and focused attention on federal tactics and objectives. At the time he took his life, Swartz was facing a potential sentence exceeding 50 years—for attempting to release scholarly articles to the public. We laid out a number of other non-hacker related instances of prosecutorial overreach by Ms. Ortiz. The article concluded that Swartz’s treatment wasn’t anomalous, but “a symptom of the entire disease” that underlies America’s singular status as the world’s jailer—of those who anger formidable interests, and those without friends in the right places. Brown’s case is even more egregious. As even the government itself concedes, ProjectPM comes under the definition of the legitimate practice of journalism. Brown simply harnessed information gathered from someone else’s “criminal” hack. Then he used it to expose the foul and potentially illegal activities of some of the world’s leading corporations—in partnership with secretive sectors of the government.”
Brown punctured a wall of secrecy, constructed over the past decade, that shields the state from accountability to its citizens. For that, he is threatened with a century behind bars.
His tale deserves to be told, not just because of the injustice involved. It also shows the awesome power of the Internet in adjusting the balance sheet between the big guys and the small ones. And the lengths the insiders will go to keep their advantage.
Confessions of a Dangerous Mind
In a YouTube “confession [11]” on September 12, 2012, Barrett Brown begins by explaining why he is “angry at the FBI.” A wiry redhead, Brown speaks in a sonorous baritone with a hint of Southern twang. After nervously admitting that he has a “case of the giggles” and is a recovering heroin addict, he composes himself and chronicles the story of ProjectPM and his assorted run-ins with the FBI.
Brown describes a March 2012 FBI raid on his residence in connection with alleged activities of the Internet hacker group Anonymous. With visible anger, he grouses that the criminal investigation now extends beyond him to an uninvolved member of his family.
Having received a vague warning the day prior, Brown sought haven at his mother’s house while government agents raided his apartment. Once the FBI realized the laptop they were seeking was not at Brown’s flat, they headed to Ms. McCutchin’s place (Brown’s parents are divorced), confronted her son, and—according to Brown—asked if he had any laptops he “wanted to give them.” When he responded in the negative, they left in a huff, only to return later with another search warrant—this time confiscating the sought-after laptop. As the investigation continued over the next few months, the feds could find no evidence on that laptop or anywhere else that related to criminal activity. That’s when they initiated a charge of obstruction of justice against his mother.
In his video, Brown lashed out, announcing unquestionably ominous sounding plans.
“I know what’s legal, I know what’s been done to me… And if it’s legal when it’s done to me, it’s going to be legal when it’s done to FBI Agent Robert Smith—who is a criminal.”
“That’s why [FBI special agent] Robert Smith’s life is over. And when I say his life is over, I’m not saying I’m going to kill him, but I am going to ruin his life and look into his fucking kids… How do you like them apples?”
The FBI didn’t. Later that evening, special agents, interrupting a video-chat session [12] he was having, took Brown away in handcuffs. He was held without charge for several weeks until the Justice Department unveiled the first of three indictments against him. Thus began his ordeal, and his time in custody, now approaching half a year. In the YouTube recording, Brown does not explicitly advocate violence against FBI Agent Smith, although his menacing fury does seem at the very least cause for investigation. But for purposes of comparison, it is worth noting that not long ago a Houston man received [13] just 42 months for threatening to blow up FBI headquarters in Washington, D.C. And a Pennsylvania man was recently sentenced to [14] just a year and a half for threatening to kill an FBI agent. Aside from “threatening a federal officer,” the most serious charges against Brown were laid down in the second indictment, handed up by a grand jury in December 2012. These charges related to the Stratfor hack.
The name Stratfor will be familiar to our readers. It has been in the news in the past. WhoWhatWhy recently produced an exclusive [15] investigation with new revelations on General David Petraeus’s career-ending affair—based on documents obtained by the whistle-blowing group WikiLeaks from the same Stratfor email reserve to which Brown linked.
Brown was never indicted for the infiltration, per se. Instead, he was charged with “trafficking” in stolen material and “access device fraud”—as mentioned, for posting, in a chat room, a link to the e-mail cache. Apparently, buried in the thousands of emails was the private credit card information of a number of Stratfor employees.
It was not clear how Brown’s act was singular. That same link had been previously posted innumerable times across the Internet.
All of this raises suspicions about some larger agenda in the government’s Javert-like pursuit of this young man. To understand that, we might well start by looking at how Brown came to be on the government’s radar in the first place.
Click to next: 2/4 [16]
Humble Beginnings
As an Internet muckraker, Brown had a penchant for pulling the string wherever it might lead. He was quick to take on established interests and orthodoxies, picking apart cherished truths if just to see their adherents scowl. Eventually this predilection led him to become bound up with a group [17] that made Time Magazine’s list of 100 Most Influential “People” of 2012: the hackers’ collective known as Anonymous.
The media, in referring to Anonymous, usually suggest that it is far more concrete an entity than it actually is, with “members” and a chain of command. In fact, Anonymous has no more “organization” than a group of strangers with shared interests in, say, a Harry Potter chat room. As a result, responsibility for any action attributed to Anonymous is, by its very nature, diffuse and untraceable.
What originally united “members” was immersion in a Net-centric subculture that prizes personal liberty and anonymity, if simply to exercise the right to prank people online. From this amorphous origin evolved a network of rebellious scofflaws and bored teenagers, along with a share of idealistic activists. The potential to mobilize these individuals to act in concert for a commonly defined goal is what gives Anonymous its power. Over time, a few of these digital rapscallions came to share a belief that this power can, and should, be used as a democratizing force.
Some trace the “group’s” beginning back to 2003 on the imageboard 4chan.org [18]—a forum for discussing Japanese comics. “These were just kids … interested in arcane Japanese web culture and, of course, pictures of boobs,” says Tim Rogers, author of a D Magazine cover story [19] on Brown’s Anonymous links. “They harassed people in online role-playing games and indulged in other forms of online pranking.”
Then, as now, users (now often known as “Anons”) would communicate using Internet Relay Chats (IRCs), a now ubiquitous staple of the Internet. For laymen, an IRC can best be understood like any other chat room (among other things, enabling live text messaging, privately or within groups, as well as data transfer capabilities). Whether for digital pranking, discussing the Japanese anime [20] craze, or coordinating resistance to repressive regimes, the ability to communicate and organize via IRCs has been apparent since the chats first appeared in the late 1980s. For example, during the 1991 “August Putsch [21]” by Communist hardliners against Soviet president Mikhail Gorbachev, IRCs were used to disseminate [22] information during an internal media blackout.
What eventually became Anonymous’s IRCs didn’t begin as places to plan ‘hacktivism’. They were simply digital hangouts where computer geeks could gather to discuss modes of pranking in online gaming communities. And as anyone who’s ever surveyed a comment forum can attest, anonymity gives users the nerve to say things that, for fear of reputational damage or social stigma, they otherwise never would. This admittedly mean-spirited ethos was a staple of the culture in IRCs.
“One of the things that Anonymous was at that time was an outlet [for Anons] to vent a little,” explains Gregg Housh—a once-active member of Anonymous and confidant of Brown’s. “Sociopaths seem to fit naturally into that world,” Housh says. “[It] wasn’t about activism.” As an aficionado of such activities in the online role-playing game Second Life—allegedly creating swarms of digital dildos with which to barrage other people’s online houses until their computers crashed—Barrett Brown was able to parlay his way into the often-sophomoric Anonymous fraternity.
Not So Anonymous
As a freelance writer by day and online prankster by night, Barrett Brown found himself at home among his new cohorts in the Anonymous IRCs.
Although Brown is routinely referred [23] to as a “self-proclaimed Anonymous spokesman,” he’s conceded in an interview [24] with NBCNews on March 8, 2011 that he was no such thing: “I can’t speak on behalf of Anonymous, because there’s no one who can authorize me to do that.”
Brown was dubbed a spokesman for the collective because he was one of a few willing to speak on record, using his real name, about Anonymous activities to the media. Brown is what some Anons refer to, almost admiringly, as a “namefag.” As Tim Rogers explains: “The term is not intrinsically derogatory. It just means that one has publicly identified oneself with Anonymous, using the name on one’s birth certificate.”
“I liken him more to an embedded journalist or media liaison,” explains a Kevin Gallagher, a close friend of Brown. The two met in New York City during the summer of 2012 at the HOPE9 Conference (HOPE stands for Hackers On Planet Earth), and have remained close. Since his arrest in September, Gallagher says, “[Brown] calls me on average once every two weeks.”
According to Gallagher, Brown wasn’t much of a hacker. He was “unabashedly lacking [the] skills” to access protected databases or participate in the big activities coordinated through certain Anonymous IRCs. Brown simply acted as a go-to source for media when big Anonymous operations were conducted. It was a dangerous position to put oneself into, and few did.
Ironically, Anonymous itself had security issues. “Toward the end of his freedom he seemed to be growing disappointed with the people in Anonymous,” Gallagher told WhoWhatWhy. “[Brown had] seen Anonymous become infiltrated [and] co-opted, and people choosing to become informants.”
Indeed, FBI infiltration and cooptation were able to sow discord within the ranks of Anonymous. This can be seen in the case of “Sabu”, an alleged ringleader of LulzSec—a highly active subgroup of Anonymous that coordinated many of the larger, illegal actions—turned government informant [26]. In August of 2011 he pled guilty to 12 criminal charges, and began working with the FBI to trace other LulzSec members.
After the Sabu matter exploded publicly, many members of LulzSec were arrested in the following months, and the inner circle of hackers comprising Anonymous began to fragment. But that disruption did little to lessen the underlying esprit—a strong sense of individual empowerment that came from an ability to act collectively and yet still maintain personal privacy. That diffusion of power and knowledge hindered many attempts at infiltration by law enforcement.
Simply put, few Anons actually know anything about one another, so there are few opportunities to rat each other out. It’s a setup that the Mafia would appreciate. With this inherently hard-to-dismantle structure, or lack thereof, Anonymous continues to [27] make its presence felt: on February 11 of this year, the state of Alabama’s website was hacked in retaliation for allegedly racist state immigration legislation. Personal information that was being stored by the state on 46,000 citizens was collected and supposedly deleted.
From Dennis the Menace to Robin Hood
In the latter half of the past decade, Brown, a University of Texas-Austin dropout, worked as a freelance columnist producing copy for the likes of New York Press, Vanity Fair, Huffington Post and The Onion. Channeling H.L. Mencken, Brown co-authored a 2007 book [28] titled Flock of Dodos: Behind Modern Creationism, Intelligent Design, and the Easter Bunny. Matt Taibbi, known for his stinging critiques of the financial industry in Rolling Stone, had this to say about it: “With their painstaking attention to historical detail and amusingly violent writing style, Brown and [his co-author] Alston have given the religious right exactly the righteous, merciless fragging it deserves.”
Brown’s commentary had always been attuned to civil liberties, the erosion of Constitutional rights, what he saw as an inept or complicit media structure, and the impact of the Internet on all of these issues.
As one might expect from this pedigree, Brown began writing quite favorably about WikiLeaks and pro-public-accountability forms of digital protest. Brown claimed to have been in contact with a number of the activists who in 2008 launched the first coordinated action associated with Anonymous: Operation Chanology. It began with a bizarre interview [29] that appeared on YouTube, showing actor Tom Cruise extolling Scientology that was leaked by a disaffected former church member. The Church claimed copyright violation, asserting the video was solely intended for internal distribution to church members and threatened YouTube with litigation.
When YouTube removed the video, Anonymous posted [30] their own video decrying censorship. Then Anonymous launched [31] a sustained campaign of (the now familiar) denial-of-service (DDoS) attacks against Scientology websites, together with prank calls to Scientology offices worldwide and barrages of “black faxes” that tie up receiving machines and deplete their ink reserves. Anonymous’s brand of mischievous activism was born.
 [32]The Church of Scientology fought back by publicly naming one of the publishers of Anonymous’s response video in a civil suit. That publisher was Gregg Housh. Since he had already been outed, Housh was then willing to assume the role of a go-to spokesperson (or “namefag”) for those seeking answers about the hacker collective.
[32]The Church of Scientology fought back by publicly naming one of the publishers of Anonymous’s response video in a civil suit. That publisher was Gregg Housh. Since he had already been outed, Housh was then willing to assume the role of a go-to spokesperson (or “namefag”) for those seeking answers about the hacker collective.
“I remember when we first started [targeting Scientology],” recalls Housh. “I got to this weird point only a few weeks into [the operation], where some of the teenage ex-scientologists had started convincing me of just how evil this organization was… We started thinking about this as an actual cause. From then on it just kept going.”
Housh is describing his transformation into a “moralfag,” jargon for Anons who see Anonymous as a tool for doing good and for holding powerful people and organizations accountable to “the people.”
“I was told very clearly that we needed to stop ruining [Anonymous’s] ‘bad name,’” Housh claims, referring to the immature, joker ethos that pervaded the collective at that time. “I was staring at my screen, and just thought, ‘God damn it. This is wrong.’”
All this took place before Housh and Brown met. What happened next, though, would thrust Brown into the spotlight, where he would eventually find himself in the crosshairs of the federal government.
Operation Payback
In 2010, WikiLeaks began publishing a cache of hundreds of thousands of classified State Department memos. Rattled, the U.S. government went into damage-control mode. It launched a high-stakes media campaign aiming to set WikiLeaks apart from traditional media entities, like magazines and newspapers who published the same material, in order to criminalize its actions. U.S. lawmakers and government-friendly pundits accused the website and its founder, Julian Assange, of everything from “treason [33]” (despite his not being an American citizen) to acting as a “high-tech terrorist [34].”
 [35]Senator Joe Lieberman (I-CT) used the power of his office to pressure [36] PayPal to freeze WikiLeaks’s account, to persuade Amazon to boot the site off its servers, and to get Visa and MasterCard to stop processing donations. All this despite First Amendment free-speech protections, and though neither WikiLeaks nor anyone associated with the group had been charged with, much less convicted of, a crime.
[35]Senator Joe Lieberman (I-CT) used the power of his office to pressure [36] PayPal to freeze WikiLeaks’s account, to persuade Amazon to boot the site off its servers, and to get Visa and MasterCard to stop processing donations. All this despite First Amendment free-speech protections, and though neither WikiLeaks nor anyone associated with the group had been charged with, much less convicted of, a crime.
In response, Anonymous began to organize Operation Payback. As with the campaign against the Church of Scientology, Anonymous employed what is called a Low Orbit Ion Cannon (LOIC). That’s a piece of installed software which connects your computer to a botnet—a network of computers that can be linked to obey instructions from one central authority.
Until Anonymous came along, botnets were generally assembled by bad guys, organizations like the Russian mafia, Chinese hackers. They build botnets on the sly, installing malware on computers that turns them into zombies without their owners’ knowledge. Each zombie can fire thousands of requests per second at a target website. So while you’re working on that cover sheet for your TPS report, your computer is part of a joint effort to overwhelm a company’s server and crash its website. That effort to crash a site is called a Distributed Denial of Service attack, or DDoS. The bad guys use DDoS attacks to extort money, but they can also use their botnets to send spam and steal people’s identities. In 2009, the antivirus software firm Symantec said it had detected nearly 7 million botnets on the internet.
Anonymous was the first group to build an operational voluntary botnet. By running the LOIC on your computer, you are, essentially, declaring your allegiance to Anonymous. You donate part of your computer’s processing power to the cause. That cause—or, if you prefer, the target—is determined by rough consensus among Anons.
Housh had become familiar with Brown earlier in February of 2010, after Brown published a piece [37] on the Huffington Post defending the actions of Anonymous members against the government of Australia during so-called “Operation Titstorm.” The Australian government had been attempting to ban certain forms of Internet pornography and to institute a filtering regime with which all web-hosting and search services would have to comply. In addition to the banned material, a leaked version of the proposed blacklist showed sites that had no relation to adult content. Web titans like Yahoo! and Google were against the measure. And Anonymous saw it as threatening to free speech.
While clearly supportive of the work of Anonymous, Brown’s piece was the most accurate media account of the group’s structure, aims and methods at the time:
Ten years ago it would have been infeasible for tens of thousands of individuals with no physical connection or central leadership to conceive, announce, and implement a massive act of civil disobedience against a significant Western power, crippling a portion of its online infrastructure in the process – and to do all of this in a matter of days, and without anyone involved having to contend with the tear-gas-and-horseback response with which states have traditionally been in the habit of contending with mass action. But such a thing as this is happening today, and having been done once will almost certainly be done again – repeatedly, increasingly, and with potentially significant consequences for the nation-state and implications regarding that which will perhaps someday come to replace it.
Anonymous’ current campaign is the second of its kind; the first, in 2008, targeted the Church of Scientology with DDOS attacks, a series of in-the-flesh protests outside Scientology centers worldwide, the theft and dissemination of sensitive documents, and a variety of other steps – all coordinated, or not, in a decentralized fashion that provides for no names, ranks, or central direction.
Housh was impressed with Brown’s assessment of Anonymous and called him up. Before then, “[Brown] wasn’t on any of our IRC’s, he wasn’t hanging out with Anons, he wasn’t ‘one of us,’” Housh notes. But still, Barrett Brown got it. Brown was able to take the heat off Housh, and eventually assumed Housh’s position as a media “spokesman” for Anonymous.
“In some ways, I blame myself for [the current position of] Barrett,” Housh confesses.
The danger was greater still. As “namefags,” Housh and Brown began feeling the heat now from both sides. Some Anons resented the work they were doing. Housh claims that certain Anons even handed over fake chat logs to the FBI in an effort to “prove” that he in fact ran Anonymous.
Arab E-Spring
The Arab Spring uprisings of early 2011 gave many of the idealists in Anonymous an opportunity to assert control of the brand and usher in a whole new understanding of their work. Already “namefags,” Housh and Brown continued their rise in prominence as “moralfags.” Brown was reportedly on the frontlines of Anonymous’s work in North Africa and the Middle East: taking control of and defacing the websites of oppressive governments, as well as authoring manuals on street fighting and first aid.
“During that initial stuff in Tunisia, the one thing we figured out sitting there talking to Tunisians on the ground was that a lot of the people in the streets didn’t know what they were doing,” says Housh.
“We had the ability to do some quick research and figure out what you’re supposed to be doing…[such as] wearing thin cotton garments that would tear easily when grabbed by police, or make for quick first-aid material…they would put [the information] together in PDFs. Barrett was the driving force in making these.”
It was that new guiding ethos of doing good, exemplified by Anonymous’s actions during the Arab Spring, that motivated Operation Payback. Anonymous saw financial companies that were willing to process payments [39] to the Ku Klux Klan (KKK), America’s oldest domestic terrorist organization, but not to a group ostensibly publishing government material for the public good.
In the minds of participating Anons, the decision by Senator Lieberman’s office to extra-judicially pressure those companies (and for them to comply) was fundamentally unconstitutional, insofar as donating money to organizations of one’s choice is considered free speech—an interpretation that still holds in American jurisprudence. Following Operation Payback, in January 2011 the FBI issued more than 40 search warrants in a probe of the attacks that yielded no arrests.
But the drama was far from over. Anonymous’s stature was rising; it was increasingly seen as a group that, through its mastery of the Internet, could operate beyond the reach of government and Washington’s cybersecurity experts.
Stirring The Hornet’s Nest
It was at this point that the Financial Times published an article [40] quoting Aaron Barr, CEO of a company called HBGary Federal and a “private security researcher,” in which he claimed to have identified three top members of Anonymous. When he announced plans to “out” them at an upcoming conference that month, it seemed that Anonymous had met its match.
 [41]However, Brown and Housh claimed that HBGary merely had pseudonyms, and that publicizing them would only result in people with similar names being wrongly targeted for FBI raids. Regardless, Anonymous sent out a press release (reportedly in conjunction with Brown [42]) that acknowledged its “downfall.” The press release was clearly written with a sly grin befitting Guy Fawkes [43]’s visage and a tongue firmly planted in the author’s cheek.
[41]However, Brown and Housh claimed that HBGary merely had pseudonyms, and that publicizing them would only result in people with similar names being wrongly targeted for FBI raids. Regardless, Anonymous sent out a press release (reportedly in conjunction with Brown [42]) that acknowledged its “downfall.” The press release was clearly written with a sly grin befitting Guy Fawkes [43]’s visage and a tongue firmly planted in the author’s cheek.
One day after the FT piece was published, the internal servers and websites of HBGary Federal and its parent company, HBGary, were hacked, defaced, and destroyed. Upwards of 75,000 emails were compromised and put up for public scrutiny. One terabyte of data (1,000 GB) from HBGary’s backup servers was wiped, as well as the contents of its CEO Aaron Barr’s iPad, while all of his personal information was put on the Internet. HBGary Federal’s website was replaced with a message from the hackers: “Now the Anonymous hand is bitch-slapping you in the face.” Later that month, Barr resigned.
Although this was an operation taken purely out of revenge against a smug opponent, important data emerged from the leaked emails, including evidence that a number of corporate actors, identified in the emails as “Team Themis,” were conspiring to commit a range of crimes.
The cabal involved three cyber security firms—HBGary Federal, Palantir Technologies, and Berico Technologies—all of whom are federal contractors for military and intelligence work.
The emails document a coordinated plan to pitch a “disinformation campaign” against critics of the U.S. Chamber of Commerce – a campaign with serious implications for the exercise of free speech.
 [44]The obvious news here was that federal contractors were concocting such unethical and possibly illegal plans to smear and discredit Americans. But more importantly, they had been solicited to do so by some of America’s most powerful entities engaged in an information war against their critics – and, by extension, the public.
[44]The obvious news here was that federal contractors were concocting such unethical and possibly illegal plans to smear and discredit Americans. But more importantly, they had been solicited to do so by some of America’s most powerful entities engaged in an information war against their critics – and, by extension, the public.
The Chamber is the primary DC lobbying arm of America’s largest corporate interests, such as Goldman Sachs, Chevron and Texaco. It lobbies politicians for “pro-business” trade and industrial policy, and spends more money on a yearly basis than any other lobbying organization in the country.
***
HBGary’s chief Aaron Barr may have been vanquished, but since a cursory examination had yielded information as incriminating as the Team Themis conspiracy, who knew what else was in there? The HBGary hack made clear that Anonymous needed minds like Brown’s to parse the vast resulting trove. “We brought Barrett in after that,” Housh recollects. And, according to Housh, Brown then created ProjectPM. While ProjectPM had conceptually been around since 2009 as a method [45] of “improving problems of information flow in various contexts,” it then became what it is now—a repository for studying the revealing communiques of HBGary and its associates.
The hackers and ProjectPM researchers soon hit additional paydirt. They discovered that the corporate security cowboys were also pitching a plan of disinformation and sabotage against WikiLeaks, which had publicly claimed it was in possession of a similar document cache from Bank of America (BoA). And these revelations hinted at more to come.
But because there was no formal mechanism for searching through the HBGary emails, most of the leaked documents remained unviewed and uncategorized. Brown saw this as the perfect opportunity to continue his work as a journalistic “moralfag”—digging deeper into the shadowy world of HBGary and the government’s legion of private contractors.
It’s worth noting that the seemingly reckless security firms weren’t just wild-eyed freelancers. They had in each case been recruited by a formidable middle-man. It was the classic cut-out: create deniability for the brand name corporations when the dirty work gets done.
In both cases, these three companies were recruited by the law firm and lobbying giant Hunton & Williams (H&W), which counts both the Chamber of Commerce and Bank of America among its clientele. H&W also legally represents entities such as Wells Fargo, Altria (formerly Philip Morris), Cingular, and weapons-maker General Dynamics. It lobbies on behalf of Koch Industries, Americans for Affordable Climate Policy (a coal industry front group), Gas Processors Association, Entergy (a nuclear power conglomerate), and U.S. Sugar Corp, among others.
So Anonymous and Brown were exposing the nefarious, if not clearly illegal, deeds of some of the world’s most powerful interests—outfits not known to turn the other cheek. It is this kind of challenge that may begin to explain why the full wrath of the federal government would be turned against the likes of Barrett Brown and his phalanx of idealistic researchers.
A Private Government
In a nation operating under the rule of law, one might presume that exposure of the “Team Themis” conspiracy would prompt official investigations of some sort, even if the proposed activities were in the planning stages. But the emails reveal a different role for the Department of Justice (DOJ).
At issue was the cache of documents from Bank of America that WikiLeaks was allegedly sitting on. BoA was understandably desperate to prevent their release, or at least mitigate the fallout from any revelations they contained. The big bank had a lot at stake: as of 2010, when these events were unfolding, Forbes ranked BoA [46] as the world’s third-biggest corporation. It was also one of the Big Four publicly-insured “too big to fail” banking monoliths that dominate American finance (and politics [47]).
As recipients of over $45 billion in the 2009 bank bailout via TARP (the Troubled Asset Relief Program) and given a federal insurance guarantee for nearly $120 billion, BoA was already facing a PR nightmare. It’s unclear what was in the cache of documents obtained by WikiLeaks, but it was enough to rattle BoA’s legal department, who approached the Justice Department on what to do next.
DOJ, under the supervision of Attorney General Eric Holder, recommended that BoA solicit the services of, you guessed it, Hunton & Williams.
The discussions between Team Themis and H&W involved some sordid and possibly illegal pursuits. One proposed method of undermining WikiLeaks was to “submit fake documents and then call out the error,” seemingly a plan to commit forgery and fraud—both felonies under the US code. Similar tactics to destroy WikiLeaks’s credibility were delineated in a 2008 Pentagon memo [48], which labeled the whistleblowing website an “enemy of the state.”
A ProjectPM researcher, Lauren Pespisa, told WhoWhatWhy in correspondence, “Team Themis was a collection of government intelligence contractors…hired by private clients to go after WikiLeaks, as well as labor unions who opposed the U.S. Chamber of Commerce—using offensive cyberwar techniques. They targeted many journalists and supporters of Wikileaks in order to discredit the organization, using methods most Americans would find reprehensible, and threatening to individual privacy.”
Indeed, in an email from Aaron Barr of HBGary Federal to Matthew Steckman of Palantir Technologies, Barr makes the case for subverting WikiLeaks and its supporters in the “liberal” media–and discusses plans to “attack” then-Salon columnist Glenn Greenwald.
Other tactics discussed in the emails include “cyber attacks against the [WikiLeaks] infrastructure to get data on document submitters,” noting that it “would kill the project.” Thus, the corporate representatives were advocating precisely the behavior the federal government has been on a crusade to prosecute, when others are doing it.
The conspiracy also called for “sustained pressure” through a “media campaign” to create “concern and doubt amongst moderates,” while discouraging whistleblowers by generating “concern over the security of the infrastructure,” and creating “exposure stories.”
Coordinating a propaganda campaign on behalf of clients is what firms like Hunton & Williams get paid for. But H&W explicitly solicited companies that have the technological means to violate the privacy of their targets, and quite possibly the law. The ability to “discredit” a journalist, as proposed, presumably hinges in part on blackmail material—just the type one can find in a substantive hack.
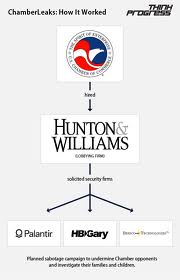 [49]The Team Themis firms solicited by H&W all do sensitive military and intelligence contracting work for the government, and in many cases are creations of the government sectors for which they work. Berico Technologies, founded in 2006 by military veterans, lists among its products the Biometric Automated Toolset (BAT), the “Army’s flagship product for biometrics.”
[49]The Team Themis firms solicited by H&W all do sensitive military and intelligence contracting work for the government, and in many cases are creations of the government sectors for which they work. Berico Technologies, founded in 2006 by military veterans, lists among its products the Biometric Automated Toolset (BAT), the “Army’s flagship product for biometrics.”
Another—Palantir Technologies—was founded in 2004 with funds from the venture capital firm, In-Q-Tel, to develop software for fraud detection. In-Q-Tel is a non-profit investment firm chartered [50] in 1999 at the request of the CIA director. In-Q-Tel’s investment is run through In-Q-Tel Interface Center (QIC), an office within the CIA. Trustees from In-Q-Tel hold executive level positions at companies such as Netscape, Sun Microsystems, Time Warner, Federal Express, ATT Wireless, and New Enterprise Associates. Most of its current investments are in the biotechnology and IT/communications industries.
HBGary Federal was the offshoot of HBGary that did direct work for the government. While privately formed by Greg Hoglund in 2003, a computer security specialist, HBGary was then acquired by ManTech International in early 2012. As one of the leading software contractors for the Departments of State, Justice, Homeland Security, and Defense, as well as the nation’s 16 spy agencies, ManTech International has seen its yearly revenue rise by more than 600% between 2001-2010. ManTech is so embedded [51] with the national security state that its employees are often placed inside the military units they support.
Flipping the COIN
The growth and ambition of the US military over the past decade has required a congruent growth in information operations against “enemy” populations. In this vein, the HBGary emails also discuss a project known as Romas/COIN [52]. Renamed “Odyssey” in 2011, Romas/COIN was a contract originally held by defense giant Northrup Grumman.
The program was a military initiative to mine and store massive amounts of data from all across the Arab world: phone calls, social media interactions, Internet searches, among other data streams. The emails discuss collaboration by over a dozen firms—all with their own niche skills—to displace Northrup and win a “re-compete” for the contract. The emails even identify household names like Google and Apple as collaborators in the scheme.
Although the re-compete was eventually cancelled, and replaced with a new contract for the program known as “Odyssey,” there’s no reason to suspect the project has been discontinued. Two days prior to the HBGary hack, on February 3, 2011, key members of the firm consortium met with the contracting officer for Odyssey at a location known as “HQ.” The trail runs dry after the email hack, which clearly derailed their potential (or at least that of HBGary) to bid on the contract. As history shows us, the employment of technologies in theaters of war always precedes their domestic importation: from the telegraph and telephone [53] in colonial Philippines to drones [54] in Pakistan and Yemen. So it should come as no surprise that this type of data mining is hardly novel or confined to a particular government agency.
 [55]National Security Agency (NSA) whistleblower William Binney has gone on record [56] stating that NSA is actively creating dossiers on every single American citizen. Lt. Col. Anthony Shaffer, a former officer in the Defense Intelligence Agency (DIA, the Pentagon’s spy agency), has noted [57] that when he served in the late-1990s his agency was actively utilizing such data-mining technology: “What we did then would take a year, you can do that in a minute [or] a matter of seconds now.”
[55]National Security Agency (NSA) whistleblower William Binney has gone on record [56] stating that NSA is actively creating dossiers on every single American citizen. Lt. Col. Anthony Shaffer, a former officer in the Defense Intelligence Agency (DIA, the Pentagon’s spy agency), has noted [57] that when he served in the late-1990s his agency was actively utilizing such data-mining technology: “What we did then would take a year, you can do that in a minute [or] a matter of seconds now.”
Digital Puppeteers
In an age of online organization and activism, how do governments discourage private citizens from such uses of the Internet? Well, a tyrant can use the mailed fist and just shut off access to it. But the more refined autocrat would simply exploit the medium to create perception of public support for their position. Enter: Project “Metal Gear.”
Metal Gear is the term given by ProjectPM’s editors to “describe any methodology or apparatus…[used] with the intent of manipulating information or perception, conducting data mining, or infiltrating social organizations.” Crucially, it involves the ability to deploy fake online personas controlled en masse by a human operator—a phalanx of Facebook marionettes to sway public opinion.
This tactic of “sockpuppeting” is hardly new. PR firms are known to routinely employ fake personas to sell products or influence viewers in online forums. But the latest software developments here are astounding, allowing for a single operator to control up to fifty online personas (at least in the case of the United States Air Force’s [USAF] contract [58] for the technology). As detailed in this 2007 patent [59], communications between the persona and its human targets can be regulated by software-based filters that assist in “maintaining situational integrity”—the puppeteer need not even move his fingers!
And these initiatives appear to be just the tip of the iceberg. Other evidence points to [60] American PR firms using digital sabotage techniques against dissidents from Bahrain and Saudi Arabia, whose U.S.-friendly monarchies happened to be their clients.
Through ProjectPM, Brown was starting to map out the web of links and business arrangements among all these private cybersecurity contractors, not to mention the non-stop revolving door for key personnel between firms and the government for which they contract. But all that spadework ended when FBI agents stormed his residence [61] on September 12, 2012.
The Mission, Not The Man
Perhaps the greatest irony in this case is the charge against Barrett Brown for “concealing evidence.” As his saga demonstrates, his real crime seems to have been revealing evidence.
Brown has been a point man in the ongoing effort to inform the American people about the consequences of the massive growth in the intelligence and military-industrial complexes since 9/11—and of the secret government at the heart of our weakened democracy.
Brown comprehended that the few avenues available to ordinary citizens for holding state actors accountable can be easily circumvented through a kind of deceptive privatization. He understood the importance of highlighting the inherently corrupt relationship between the state and the corporation. This included non-state entities handling dirty ‘official’ business on a deniable basis, and the state serving as an enforcement arm for big capital.
With much ado in recent days about Chinese cyber espionage [62], the government is using this new “Yellow Peril” as an opportunity to mount a full court press against the ability of any group to maneuver on the Internet in ways that might threaten corporate and state interests. The White House just announced a new administration-wide strategy [63] to identify and prevent the theft of trade secrets, labeling WikiLeaks, LulzSec, and associated ‘hacktivist’ groups as dangerous in this regard.
“Disgruntled insiders [may leak] information about corporate trade secrets or critical U.S. technology to ‘hacktivist’ groups,” the document warns. The language is instructive; it makes no distinction between groups that may be receiving such leaked information to sell to the highest bidder and groups that want to release the information to the American people in order to blow the whistle on ‘insider’ waste, fraud, abuse, or illegality.
 [64]Brown, and those close to him, also understand what the government was truly after when they stumbled into his life in March of 2012. The charges against Brown for harassing a government official, obstructing justice and concealing evidence may seem unrelated to his journalistic work, but the initial search warrant issued for his home on March 6, 2012, cast an ominously wide net. “The entities listed [there] are all things ProjectPM was looking into,” Gallagher confirms. “ProjectPM is [now] mostly defunct without [him].”
[64]Brown, and those close to him, also understand what the government was truly after when they stumbled into his life in March of 2012. The charges against Brown for harassing a government official, obstructing justice and concealing evidence may seem unrelated to his journalistic work, but the initial search warrant issued for his home on March 6, 2012, cast an ominously wide net. “The entities listed [there] are all things ProjectPM was looking into,” Gallagher confirms. “ProjectPM is [now] mostly defunct without [him].”
Citing the extraordinary charges and the zeal with which the feds are operating, Brown’s supporters have set up a website [65] to collect donations and fund a proper legal defense for him. With Brown in custody, much of his work has stalled. “[ProjectPM] was Barrett’s baby,” Lauren Pespisa laments. Although other websites such as Telecomix’ Blue Cabinet Wiki [66] are attempting to pick up and expand on ProjectPM’s work, “that IRC has been suffering massive DDoS [attacks] and is very quiet. I fear ProjectPM may have been something special, I haven’t seen anything replace it yet.”
At our publication deadline, ProjectPM’s site was down for unknown reasons.
# #
Back to Page 1 [67] 2 [16] 3 [68] 4
Graphics Credit [69]